IIC: The Endpoint Security Best Practices White Paper
The Industrial Internet Consortium published today the Endpoint Security Best Practices white paper. The intended audience includes industrial equipment manufacturers, integrators, and industrial equipment owners and operators. All can benefit by obtaining a clear description of what countermeasures and controls are generally recommended for each level of security. Equipment manufacturers and integrators can define which security level their products, systems, and solutions are designed to meet. Insurers and policy makers may benefit by having a common benchmark that can be used to analyze risk and encourage security improvements. And while this document is not intended as the basis for certification or as a checklist, certifying organizations may wish to review it as they develop their own certification programs.
The common uses of this document are illustrated in Figure 1:
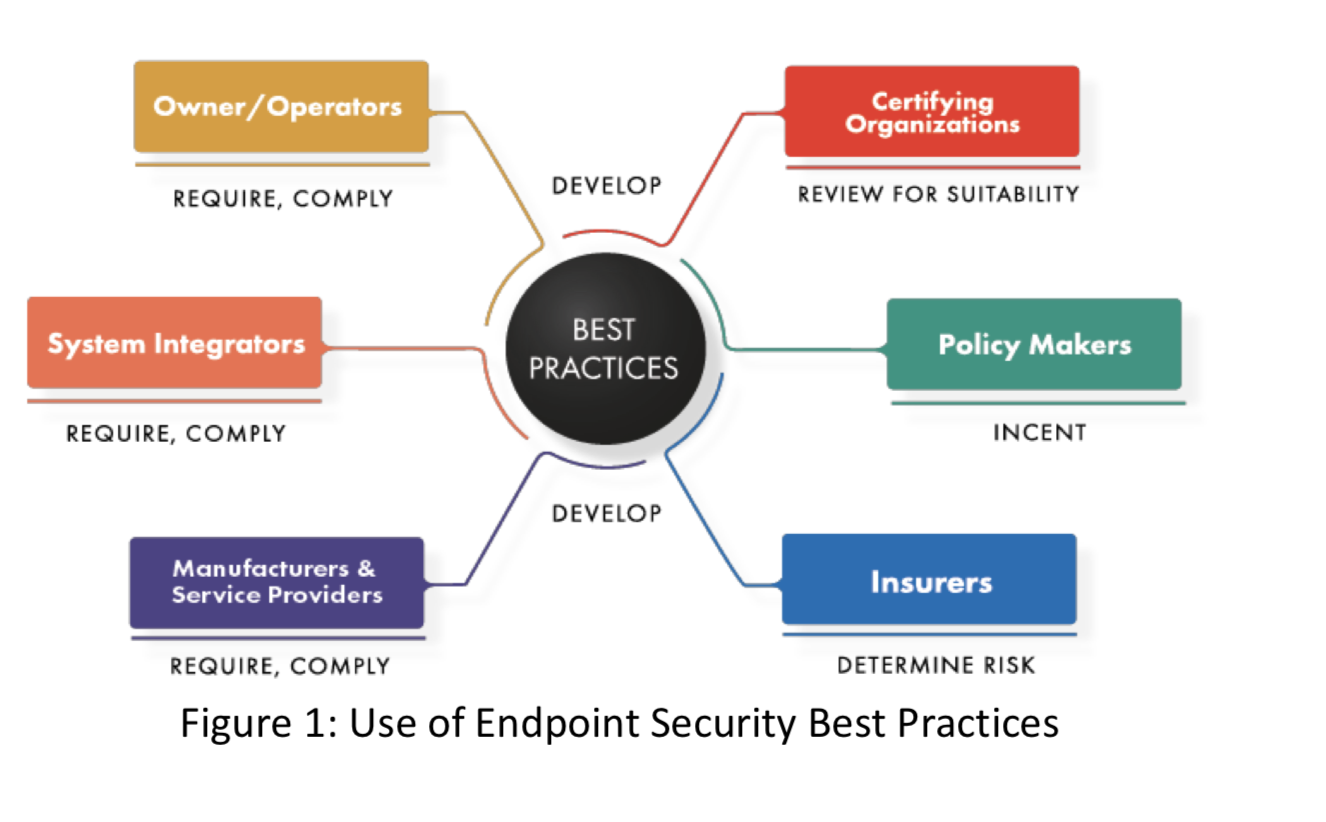
While regulations may compel some organizations to comply with industrial security requirements, those who are not subject to regulation should still pay attention. Poor industrial security has direct negative effects such as safety problems and equipment damage, and indirect effects such as customer dissatisfaction, poor quality and reliability, possible liability, and eventually reduced profits. Conversely, good security can drive a virtuous cycle of reduced costs and increased reliability and safety.
The best practices listed in this document are horizontal, not tuned to the specific needs of one sector such as manufacturing or transportation. Readers may need to adjust these practices to reflect sector-specific requirements or regulations. Future editions of this document may contain sector-specific sections. Absent such guidance, these best practices provide field-tested advice that can be used across sectors, in conjunction with a careful risk analysis.
Because of the difficulty of modifying existing deployed endpoints to increase their security, this document is primarily targeted at new endpoints. However, some of the core concepts included here (e.g., tamper resistant change controls) may be valuable for legacy endpoints. Endpoints should include secure update capabilities but inevitably as endpoints age they will eventually become legacy endpoints. For legacy endpoints with inadequate security, other security measures such as network security must be employed.
The paper explores one of the six functional building blocks from the IIC Industrial Internet Security Framework (IISF): Endpoint Protection. The 13-page white paper distills key information about endpoint device security from industrial guidance and compliance frameworks, such as IEC 62443, NIST SP 800-53, and the IIC IISF.
The full Endpoint Security Best Practices white paper and a list of IIC members who contributed can be found here.



