Protecting Smart Buildings from Cyber Attacks
It was an attack on a hospital like no other, reported the news in February 2016. The Hollywood Presbyterian Medical Center had been hacked. Its services were crippled. As emergency patients were diverted to other area hospitals, hospital administrators received an ominous message. Pay a ransom to get your hospital systems back. The hospital ultimately paid $17,000 worth of bitcoins. The FBI and the Los Angeles Police Department have yet to find the culprit.
The hospital attack brings to light just how vulnerable buildings and institutions are to hackers. For hospitals, it can cause a disruption of medical services that could include blocked access to patient records, laboratory results, surgery and critical patient information updates. The potential cost in lives and loss of public trust is on par with what might occur with significant natural disasters.
IoT Smart Technology and Risk
Over the past few decades, there have been a number of seismic shifts in technology. Mainframe computing, client/server and cloud computing are some examples that easily come to mind. The emergence of the Internet of Things (IoT) has seen a technological shift that could potentially change the way our society operates.
The emergence of the IoT will affect urban planning and engineering as much as it will impact network computing services. The IoT and smart building technologies will be at the core of the smart cities we live in, the smart buildings we occupy, and even the smart bodies we inhabit. More about The Smart City Ecosystem Framework – A Model for Planning Smart Cities
The construction and engineering industries will be significantly disrupted as the IoT transitions from a new technology into a standard feature of the built environment. While a building that fully integrates your preferences and activities can offer almost limitless opportunities, this shift can also expose buildings and all those associated with them to the increased likelihood of cyber-attacks.
Industry predictions suggest that by 2020, there will be an installed base of some 30.7 billion IoT devices. Many of these devices will be deployed within smart buildings, critical infrastructure and public works. Engineering professionals have previously been largely ignored by cyber criminals and Internet-based security threats; however, as engineering firms find themselves with a much greater online presence, and as the technological integration of the occupant and the built environment gains momentum, cyber criminals are now placing a much greater focus on buildings as the targets for their attacks. Engineering firms can no longer simply hope to be ignored by these groups, as their intellectual property has become a much sought-after commodity by criminals.
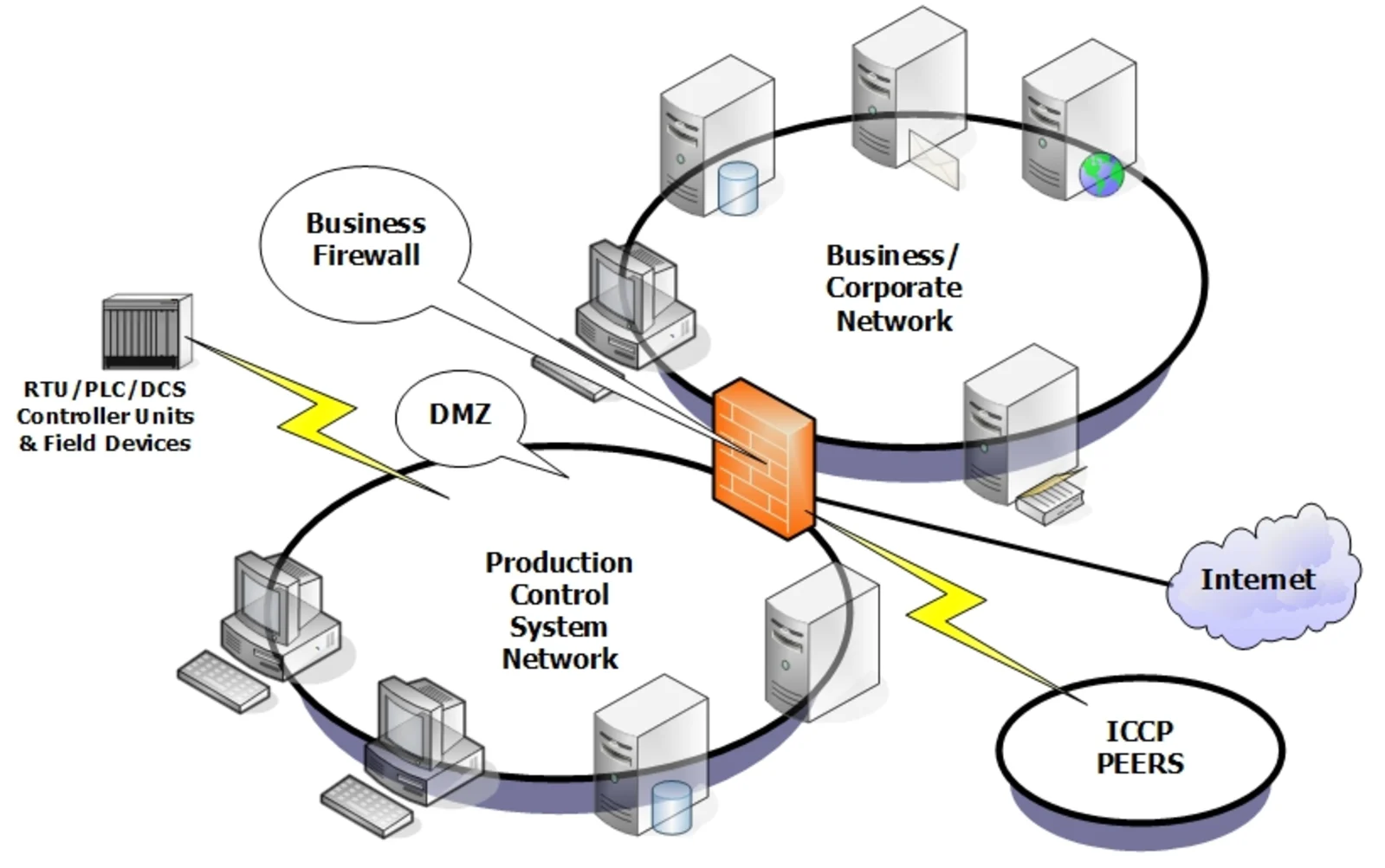
An image of a Control System as a DMZ. (Image courtesy of ICS-CERT.)
Closing the Gap Between Corporate and Control Domains
Historically, the control systems domain was protected by physical separation. The corporate domain was segregated from the control systems domain,which created a break in outside accessibility that was generally adequate for the time. However, as global services delivery, data sharing and data acquisition became critical functions within modern business and technology markets,this model was no longer sustainable.
The requirement for cost-effectiveness and modern system architectures saw system owners moving toward interconnected technologies. These technologies provide asset owners with access to open architectures and improved communication technologies that were not previously available. The benefits were immediate and significant, with improved efficiency, operation and analytics available to assist the asset owner to help ensure that their building performed according to their requirements. Of course, with these connection opportunities came an increased risk exposure to attack scenarios and exploits from external sources.
Cyber criminals who had previously concentrated on enterprise networks and online service are now targeting industrial control systems (ICSs) at an increasing rate. The stakes are extremely high. Bringing down a retail website isn’t the goal of the criminal online presence any more. They can now target critical infrastructure, such as hospitals, government departments and power stations.
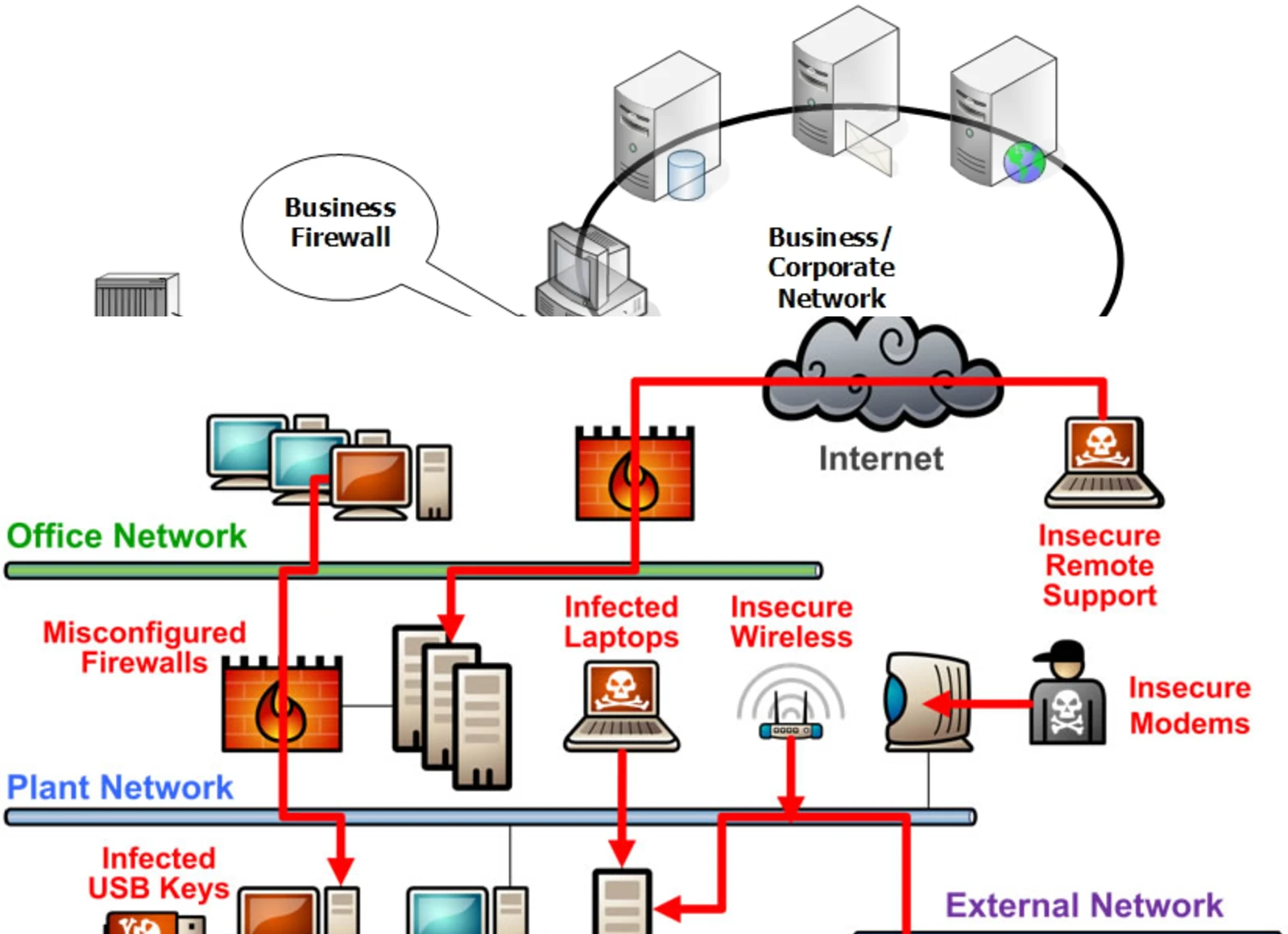
Pathways for intruding the control systems environment. (Image courtesy of the InfoSec Guru.)
Government and Military
Prior to the Stuxnet attack, very few outside the engineering profession had heard of a programmable logic controller (PLC), let alone what its purpose might be. In 2010, the Stuxnet virus targeted industrial computer systems across the globe and caused significant damage to critical infrastructure, notably to an Iranian nuclear power plant.
Stuxnet specifically targeted PLCs, which in general allow the automation of industrial processes such as those used to control machinery on assembly lines and heating, ventilation and air conditioning (HVAC) systems. Stuxnet affected the centrifuges for separating nuclear material. Exploiting system flaws, the virus targeted systems using the Microsoft Windows operating system. Once established on the network, Stuxnet sought out Siemens STEP 7 software. The compromised Iranian PLCs caused the nuclear plant’s centrifuges to behave erratically. The resulting damage forced the centrifuges offline and caused a major delay in Iran’s nuclear program.
Clearly, this created disruption on an unprecedented scale. The convergence of technologies and shared network communications provided an opportunity for state-sponsored cyber warfare. This may have been the first attack of its kind, but it certainly will not be the last.Overnight,industrial control systems were on alert. This was not just a concern for power plants and government infrastructure. Possible victims could include medical facilities, entertainment complexes, smart buildings and public infrastructure. With Stuxnet, the world experienced its first industrial-scale cyber warfare attack, and unlike conventional warfare, the perpetrators achieved their goals without even a hint of detection. The target was a building, specifically its centrifuges. The payload was a virus transmitted via the network, which was capable of mass destruction. A building’s engineering blueprint had become a weapon of attack.
It’s possible that some engineers may consider these scenarios to be more Hollywood blockbuster than real-world possibility. This line of thinking is now considered shortsighted in many industry circles. Building and engineering clients are increasingly aware of how their brand and services can be exposed in an all-connected, always-on digital age. The need for cost-efficiencies have increased the risk exposure that providers and asset owners are facing. The benefits of IP convergence are considerable, but they do come at a “cyber risk” cost.
Of course, the best cyber security strategy can be worthless unless it is integrated into a holistic security approach. All the password and cyber protection isn’t of much use if someone leaves their laptop logged in while they mingle at a conference. Creating a robust cyber security system involves ensuring that physical security is addressed, along with adhering rigorously to sound digital security processes. Only when digital, physical and cyber security are working together can an asset truly be considered secure.
More about Industrial IoT Security Challenges
Increasingly, organizations are looking at designers and engineers to factor these concerns into their engineering designs and specifications. Clients know they are exposed. The continued growth in organizations seeking comprehensive and expensive cyber insurance clearly highlights this point. It is not solely whether the end product is functional, innovative and cost-effective that drives the client’s selection process. It’s increasingly about their risk profile.How will it hold up to a cyber attack? And if it does not, how will this affect baseline operations?
Facilitating and Monetizing Cyber Attacks
Cyber-attacks were once all about “sticking it to the man.” The attacks were usually commercially or politically motivated, and the outcomes where generally the same: public release of commercial software or the disclosure of classified information.
Today, attacks are just as likely to be about extracting the best possible ransom in the least possible time. Cyber criminals are often working with organized crime and are using the convergence of technologies to access ever-increasing critical services and sensitive information to extract a substantial toll. They know that every moment that a critical technological element is down, such as an investment banker’s trading floor or a critical government department, the cost to the party being attacked begins climbing. It is the critical nature of these services that has changed the playing field. Cyber criminals know that they have a good chance of receiving ransom if the cost of fighting an attack is much greater—and the cost of a successful attack on a big business can be astronomical. To aid in these attacks, cyber criminals are sizing up urban planning and design, seeking soft points to launch new cyber-attacks.
Security by Design
In an IoT world where a camera or building management system (BMS) can potentially launch a cyber-attack and disable a building’s critical services, there is an imperative to address these risks at all levels of the build, design and deployment stages. Builders, engineers and critical services specialists who do not factor in potential cyber risk threats as part of their design considerations expose their assets, their occupants and the public to considerable risk. This is not to suggest that engineers are required to become cyber security specialists; however, it does imply that urban planning, design engineering and automation processes need to be considered and factored into the overall cyber world ecosystem.Put simply, the inclusion of smart technologies within building services and design considerations requires a collaborative approach to help ensure that security and privacy standards are maintained.
This collaboration must extend to electrical and mechanical engineers, HVAC, fire safety, BMS, and audiovisual specialists. Whether engineering companies work in collaboration with cyber security firms or build out their own competencies, the need for an integrated approach to cyber security challenges is required.
IoT Cyber Frameworks—A Need for Cyber Industry Engagement
Many cyber security experts have long identified a need to bring more than just words to the critical infrastructure and IoT security design table. Urban planners and engineers need collaboration tools, methods and frameworks to make their buildings more cyber safe. These frameworks are long overdue. Recently, industry bodies such as the IoT Security Institute (IoTSI) has released a global, publically available IoT cyber security and privacy framework for buildings and critical infrastructure. The objective of such foundations is to open the channels of communication between engineers, designers and urban planners when it comes to the cyber security challenges affecting build and critical environments. In addition, the IoT Security Institute acknowledges the collaborative benefits of working with those who build smart cities, enable Industry 4 technologies, and facilitate their deployment. These enablers advise civic leaders and organisations on emerging trends and business opportunities. They play a vital role in the conversation.
At the IoTSI we quickly recognised the success of any IoT Security Framework depended on working with an array of players and stakeholders within smart technology eco-systems. We are constantly fostering working relationship with the broader smart technology industry, Our objective is to better align cyber and privacy controls from design to build completion. A security and privacy by design approach.
The cyber security industry is establishing a presence within the smart building and critical infrastructure markets at a rapid pace. The future of smart urban planning will usher in an era of possibilities, functionality and convenience that can provide unprecedented opportunities. These opportunities will need to be protected. As the public and private sector transition to smart city ecosystems, the insistence and maintenance of cyber safety and privacy will be critical, whether at the HVAC system, smart parking station, industrial plant or a child’s Internet-connected smart toy. As the IoT becomes a common part of building design, businesses that work in the built environment must give cyber security as much consideration as they would the structural integrity of a building.
![]() This article was written by Alan Mihalic, the President of IoT Security Institute. He is a senior Cyber Security Advisor and Risk professional with demonstrated expertise and success in cyber security, ICS security, cyber practice development,risk management, security architecture methodologies and principles supporting strategic enterprise security initiatives.
This article was written by Alan Mihalic, the President of IoT Security Institute. He is a senior Cyber Security Advisor and Risk professional with demonstrated expertise and success in cyber security, ICS security, cyber practice development,risk management, security architecture methodologies and principles supporting strategic enterprise security initiatives.


