How will US sanctions on the group behind TRITON protect critical infrastructure?
In late October 2020, the US Federal Government announced plans to impose sanctions on a Russian research institute that has been linked with cyber-attacks. The institute is alleged to have played a part in building the customized tools used in the TRITON malware targeting Industrial Control Systems (ICS). These sanctions are part of a wider US Government campaign to disrupt cyber-attacks backed by nation states and large organized crime groups.
TRITON uses a sophisticated set of tactics to maximize its stealth and its potential to do damage. The attack was first observed ‘in the wild’ when it struck a Saudi petrochemical plant in 2017. TRITON has been called ‘the world’s most murderous malware’ due to its potential to cause massive failure in industrial environments by targeting safety systems, along with compromising other critical industrial operations.
Timeline of TRITON
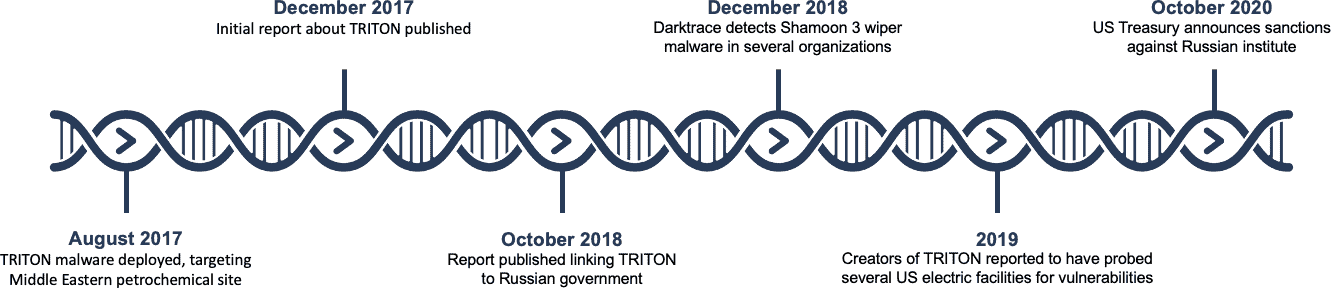
Figure 1- A timeline of the TRITON attack
The significance of TRITON
TRITON has been identified as an Advanced Persistent Threat (APT), meaning that it is a state-sponsored attack distinguished by its high threat level and novel vectors of attack. It was designed to give the attacker complete control over infected systems and enable tampering with industrial controls.
The malware utilized state of the art tactics, techniques and procedures (TTPs) in order to remain undetected, evade security defenses, and achieve the attacker’s goals. Like recent attacks against operational technology (OT) such as EKANS, TRITON exploited the convergence of informational and operational technology (IT/OT) by initially compromising enterprise devices before pivoting into OT subnets.
This chain of compromise is similar to other high-profile OT attacks, such as Havex, Stuxnet, and Industroyer. In fact, Darktrace detected a similar APT, Shamoon 3, when it impacted several firms in the Middle East in December 2018. While this strain of malware didn’t specifically target OT systems, it used similar TTPs to infect and deploy a strain of wiper malware, which wipes the hard drive of the infected device, and typically targets critical infrastructure.
Along similar lines, the US Government reported that at least 20 American electric facilities had been probed for vulnerabilities by the same authors of TRITON based at the Russian Institute in 2019. These activities demonstrate a general increase in OT attacks targeting critical infrastructure backed by nation states.
The evolving threat landscape
The knock-on effects of US sanctions
The recent sanctions are designed to disrupt the actions of active threat groups and to deter would-be attackers. A secondary goal is to raise awareness within the cyber industry and the general public as to the types of cyber-threats faced by critical infrastructure. The sanctions are likely to slow attackers, but not stop them. Indeed, nation states are well resourced and have strong motives, and APT hacker groups will continue to adapt and innovate.
The future of OT attacks
Attacks like Shamoon and EKANS ransomware have demonstrated how IT/OT convergence has made critical infrastructure vulnerable to non-OT targeted attacks. However, there is another development that is emerging on the threat landscape, one that will likely only further the destructive potential of OT attacks. This development is the malicious application of machine learning and other AI technologies to cyber-attacks, otherwise known as ‘offensive AI.’
For OT-specific attacks, APT groups are likely to adopt machine learning and AI techniques to stay ahead of defenders. This would allow attackers to better exploit IT/OT convergence and pivot quicker into OT systems. In other words, with the help of AI and machine learning, malware will be able to autonomously find its way to its target, learning the ins and outs of complex infrastructure in order to strike the right target at the right time.
A highly effective use of machine learning will be to train malware in optimal decision-making. For example, supervised machine learning can transfer the skills of the best malware operators directly into the malware itself. This greater autonomous ability within the malware will allow it to delay establishing a command and control (C2) connection.
Trained malware can operate independently until, for example, it is able to communicate with an OT control system. Establishing C2, performing OT reconnaissance and exfiltrating the results can then be completed extremely rapidly, far too fast for humans to mitigate the threat even if it was spotted immediately.
Future OT attacks targeting critical infrastructure are likely to incorporate several of these techniques. The TRITON framework, for example, required operators of the malware to manually trigger its functions through scripts. In the future, we can conceive of an AI-equipped version operating without command and control, perhaps only calling back at the end of the reconnaissance phase.
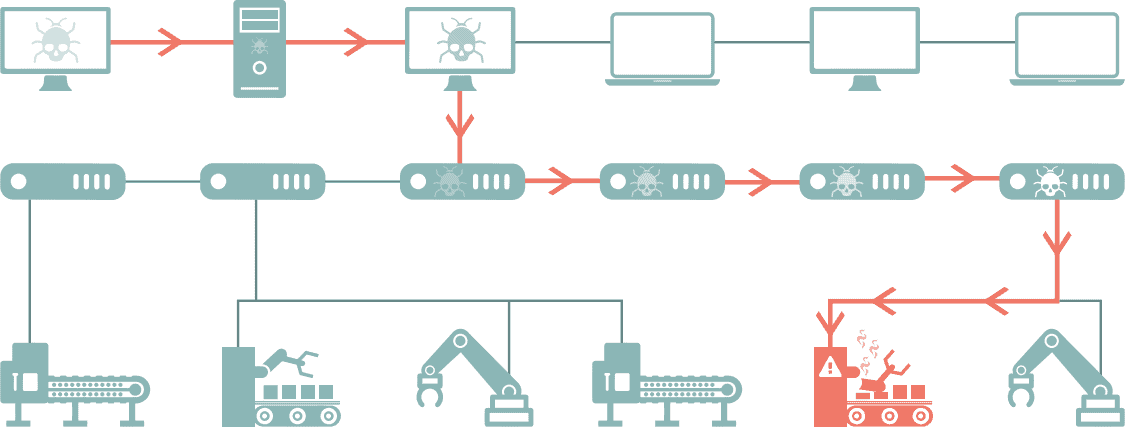
Figure 2: AI-enabled malware is able to autonomously find the optimal path to its ICS target
Concluding thoughts
It is becoming apparent that OT attacks are increasingly being carried out by nation state backed hacking groups. These hacker groups have access to cutting edge malware tools to ensure the attackers can remain undetected, evade security tools, and achieve their goals. Indeed, these state-sponsored attackers appear to be getting more aggressive and audacious in their attempts. The sanctions are a step in the right direction, but only a robust defensive strategy will ultimately keep targeted infrastructure from being damaged by these threats.
State-sponsored cyber-attackers are combining the skills of IT and OT malware authors to exploit IT/OT convergence. The attackers are also exploiting weak spots in legacy approaches to security. For instance, many organizations use separate IT and OT security teams as well as distinct IT and OT security tools. This arrangement ultimately creates blind spots in cyber defenses.
The use of AI malware is likely to be part of the evolution of OT attacks. Only security teams equipped with AI themselves can expect to defend against these types of attacks. Darktrace enables IT and OT security teams to better collaborate and protect against these advanced persistent threats to critical infrastructure. Indeed, Darktrace has already caught APTs in the wild, without relying on any prior threat intelligence, but instead by learning ‘normal’ for every user, device and controller and identifying anomalous behavior that arose as a result of the attack.
As APTs such as Triton eventually get an update, and incorporate more innovative technologies into their TTPs, Darktrace builds resilience by learning the DNA of industrial infrastructure, illuminating any possible points of convergence between OT and the corporate network. By automating investigations and spotting all anomalous activity in real time, Darktrace augments human teams so that they stay one step ahead of tomorrow’s attacks.
Thanks to Darktrace analyst Oakley Cox for his insights on the above investigation.
Read more about the Industrial Immune System
About the Author
 This article was written by David Masson. He is Darktrace’s Director of Enterprise Security, and has over two decades of experience working in fast moving security and intelligence environments in the UK, Canada and worldwide. With skills developed in the civilian, military and diplomatic worlds, he has been influential in the efficient and effective resolution of various unique national security issues.
This article was written by David Masson. He is Darktrace’s Director of Enterprise Security, and has over two decades of experience working in fast moving security and intelligence environments in the UK, Canada and worldwide. With skills developed in the civilian, military and diplomatic worlds, he has been influential in the efficient and effective resolution of various unique national security issues.



