ICS Cybersecurity Day 2021 – Answers to your questions from Quantalytics and Trend Micro
Thank you for your active participation at ICS Cybersecurity Day. As promised, here are the answers to your questions (those that were not answered live during the event).
Q1. What solution do you propose for old equipment that have old versions of windows/software, which are no longer supported and need to be connected to the internet and be able to access them remotely. There are many companies that have this type of equipment and cannot afford to replace all these devices with their latest versions. Not to mention that the software that is being developed now will be obsolete in a few years.
Answer by Arthur J. Carp, Quantalytics, Inc.
Adding Network Access Control will allow you to closely control:
• What other devices have actual access to these legacy devices
• What users have access to these legacy devices
• What services on these legacy devices are available to the predefined users above.
You will be able to lock down access by MAC Address as well as IP Address. (whitelist.)
You will also need a proxy server. The Proxy Server will allow you to control what external IP addresses are allowed, as well as protocols. Plus priviledges. E.G. Read only.
PLEASE NOTE: There is a better way to get info OUT from these legacy devices if you only need to monitor them externally. MQTT protocol combined with a Proxy Server. Our Q-Communicator is one such example. Many people, including OT, are not familiar with the MQTT protocol.
MQTT protocol link.
Answer by Trend Micro
Besides using NAC, there are many other purpose build ICS security solutions in the market today to provide visibility, prevention, and protection for these types of environments.
For example:
1. Visibility part – you have many companies like Nozomi Network, Forescout, Trend Micro, etc. These companies provide you visibility for all your OT devices.
2. Prevention, protection – TXone Network, Trend Micro, Fortinet, CISCO. These companies have IPS/IDS, Firewall capabilities that allow organizations to deploy on a one-to-one relationship or one-many relation. Or you can do network isolation and segmentation using these effective solutions.
3. Other very effective solutions in securing these types of systems are lock-down or white-list capabilities, which can support many operating systems like XP, Windows 7, even Windows 2000, etc. A few companies offer these: Trend Micro, esTxone Network, and McAfee.
Q2. With today’s proper security programs and zero trust, do you need honey pots (sic) to some (sic) point?
Answer by Quantalytics, Inc.
In our opinion, yes. Honeypots provide:
a) network obfuscation – hiding assets in plain sight;
b) a tripwire (burglar alarm) in case the hacker gets past IDS, and
c) shifts the odds in favor of defense.
A honeypot can be configured to show, for example, 100 identical PLC attack surfaces. This leaves the hacker with a problem: 101 PLCs are apparently on this network, and if he scans the wrong one (100 chances), an alert will be triggered. The only reason someone would be scanning these attack surfaces would be to potentially hack them. There is no legitimate reason to try to find open ports or connect (e.g., telnet) into them. The odds have been shifted from 1 to 1 (no honeypots) to 1 in 101 (with honeypots)—clearly, a radical improvement for defense.
The only limit is the number of LAN IP addresses available to assign to the honeypot attack surfaces. With a Class B network, one could have literally thousands of honeypot attack surfaces per real OT device or network service.
A state-sponsored hacker will resort to passive listening on the network to try to find the legitimate target(s). However, this takes time, and increases the odds of getting caught through legitimate network scanning.
Honeypots add a crucial, and currently missing on the vast majority of networks, a layer of defense.
Answer by Richard Ku, Trend Micro
Honeypot is only one means of a tool that organizations can use to test how vulnerable they
are. The most effective way is to focus on the following areas and continue to improve on them so your security posture can get better each day.
My four key pillars to a successful cyber strategies are:
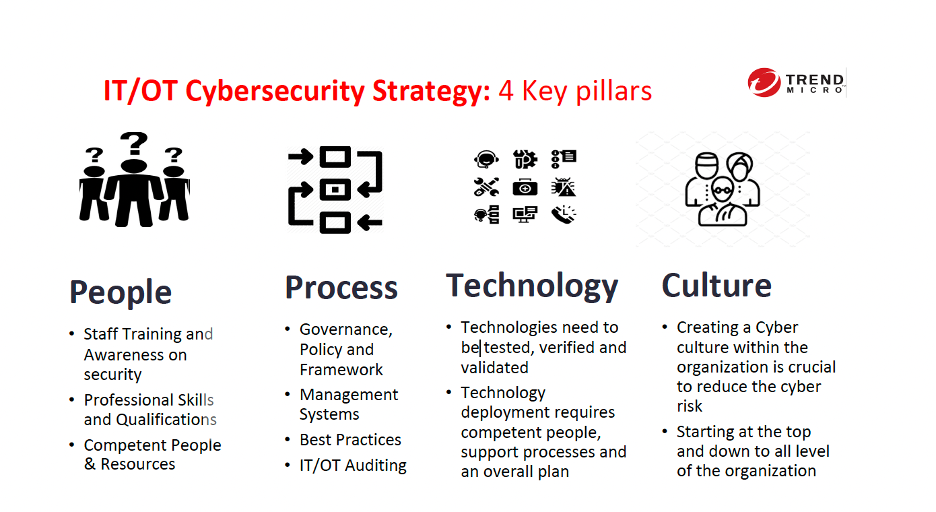
Focus on these key areas and the organization security posture will be better.
Q3. As an Engineer, and sometimes OT, how do I engage my IT in security? We been going through growing pains. Our once fairly open network is being closed off. This of course breaks things. What can I do to work with my IT to secure the infrastructure, but not loose (sic) my mind
Answer by Arthur J. Carp, Quantalytics, Inc.
You need an inter-disciplinary approach. I suggest you form a joint working group, even if it is just 2 people – you, and someone from IT security to CLOSELY work with you. You will identify devices and services and provide EXACT instructions to IT as to what access is needed to either the device, the service, or both, and by what user(s).
The more closely you can define the parameters of device, service, and users (w/priviledges; e.g. read-only, read-write), the more closely they can use existing IT tools, or acquire same, to control the parameters. We always see a communication problem between OT and IT people. Very few bridge both. However, the more closely you can define your devices and their network services and users, the better IT can understand. N.B. When you define services, include ports used if tcp.
Answer by Richard Ku, Trend Micro
The convergence of IT/OT has created challenges between the two organizations. The key to success is communication, collaboration, and the willingness to work together and share knowledge and expertise across both organizations to address the cyber challenges. No one organization will know everything, and building/creating a small cyber security project together will be a good start.
Q4. Are the datasets from the honeypots available to members or the public?
Answer by Arthur J. Carp, Quantalytics, Inc.
All data is private if you run your own honeypots. If you have multiple honeypots on multiple private networks (e.g. multiple power plants), you can also have a PRIVATE honeynet. The information collected from either a single honeypot or a honeynet can be fed into:
1. Log Analysis
2. SIEM
3. Threat Intelligence (e.g. MISP – Malware Information Sharing Platform).
Threat intelligence can tell you if one honeypot is hit, what to look for on the other networks even if no alarm has been triggered yet, or at all.
Answer by Richard Ku, Trend Micro
There are many organizations and groups that have this database to share across different verticals or groups. Shodan is a public site, and I mentioned it in the panel discussion. You can see all the exposed IP addresses that the adversary could potentially compromise. Trend Micro has also published a white paper study on the honeypot we created for a smart manufacturer. I am happy to share a copy of our research and white paper if interested.
Q5. Do you feel as though the industry suffers from not performing backup procedures correctly? To include backup verification/validation.
Answer by Arthur J. Carp, Quantalytics, Inc.
The issue we see is insufficient “fire drills”. Regularly testing RESTORATION. A backup can be valid, but the restoration fails. E.G. hardware changes between backups. Regularly test restorations on test hardware. We recommend whenever possible to have a hardware lab so that tests can be run against hardware. The alternative is virtual emulations.
Q6. Can you guide on any standard certification or studies for getting expertise on IIoT cybersecurity? Shekhar here from Mumbai, India. CEO, GrassDew IT Solutions (Its 12:15 am night here) ☺️👍
Answer by Arthur J. Carp, Quantalytics, Inc.
The SANS Institute is one classic route. Their certificates are held in high regard. Please note that I and many others are self-taught. In my case, my experience pre-dates the creation of certifications. Another route is to try to persuade a college to create a joint program between the Computer Science Department and an Engineering Dept. (e.g Chemical Engineering) for an interdisciplinary degree where one studies cyber security (Comp Sci) and applies it to Engineering (Chem E.).
Answer by Richard Ku, Trend Micro
The key to a successful cyber strategy is to ensure you address the four pillars I mentioned above: People, Process, Technologies, and Culture. And device manufacturers need to put secure by design and part of their development life cycle. Organizations need to set a high priority on the budget and resources to address this. It can not be an afterthought, a secondary plan, etc.
The Big Picture: Effective OT/ICS security begins with understanding the big picture. The SANS 2019 State of OT/ICS Cybersecurity Survey offers profound insight into many aspects of protecting your company from the increasingly real risk of both accidents and attacks that threaten ICSs every day.
People: People play a critical role in a cyber strategy. A trained and security-aware organization can reduce security risk significantly. The organization needs to develop appropriate cyber security training and other people skills as integration is required. A 2019 SANS study indicated that over 62% of respondents consider the human factor the most significant risk to their operations, yet most security budgets for this category don’t exceed $100,000. This is a blind spot for many organizations, and this needs to become a more significant focus for the organization if it is expected to be successful. Investment into cybersecurity strategy should always begin with people. However, differing roles and unclear responsibilities among staff can make things difficult. Consequently, it is essential to set specific rules and align business concerns with the current threat environment. An excellent place to start is with defined cybersecurity training. Survey respondents named this a top business initiative for 2019, with 29% of companies stating they would be investing in more training for IT, OT, and hybrid IT/OT personnel.
The Process: For a cyber strategy to be effective, the organization must develop and implement processes and procedures, ensuring clear roles, responsibilities, and management systems are put in place. In addition, the Process needs to include governance, policy, and best practice framework and must be periodically tested to ensure it is effective. If the Process is forgotten or broken, it can lead to potential cyber risk. The 2019 SANS study found that only 14% of the respondents perceive Process as the most significant security threat. Therefore, almost half of the respondents are budgeting less than $500,000 for its Process in 2019. Identifying weak links in the Process should be a priority, not an afterthought – and the Process needs to be extended across the ITOT convergence environment.
Technology: The lack of understanding of appropriate OT technology deployment has led to many control system cyber incidents resulting in downtime or even creating safety challenges for organizations. For example, deploying an IT vulnerability scanner into an OT environment can cause the process control system shutdowns because of incompatibility of protocols, type of application running, or operating systems. In the 2019 SANS study, about 22% of respondents consider technology deployment as one of the significant security risks in their operation.
Culture: Creating cyberculture within the organization is crucial to reduce the cyber risk to the company. This culture must start from the top and be communicated to all levels of the organization. For the OT environment, this includes the Engineering and Operational organizations responsible for the equipment being secured.
Q7. Are organizations not completing contingency testing to test IR, etc.? There seems to be a lack of tabletop exercises for ransom attacks
Answer by Arthur J. Carp, Quantalytics, Inc.
Some industries, such as the Power Generation and Transmission Industries in North America, have mandatory tabletop exercises periodically. (FERC & NERC.) This is by law. Most industries do not and should. They should be used to test previously drafted contingency plans (playbooks) drawn up beforehand. This should include the involvement of the Legal Dept. and Investor Relations, if publically held. Everything should follow a script, down to the last check box on a checklist, for a response to a ransomware attack. We can only expect more ransomware attack attempts, and more successes if defenses continue to lag more and more, as is the case, sadly, currently.
Q8. Cybersecurity has been mostly reactive step. What is the reason behind it? Is it lack of responsibility? Or is it lack of insecurity? Or investing in features will give better results than investing in Cybersecurity?
Answer by Arthur J. Carp, Quantalytics, Inc.
We are typically reactive because defense always lags offense. The classic example: 0 Days vulnerabilities. Unknown, and therefore, no defense. We have in the OT world the problem of timely (immediately) patching. Sometimes it is not possible until scheduled maintenance of the equipment. This means “watchful wating”, which in turn, means being vulnerable. To decrease vulnerability, IT monitoring tools (e.g. IDS, Log Analysis, SIEM, and Honeypots need to be used.
Part of the problem is responsibility. IT does not understand, and OT jealously guards its turf out of fear that IT will impact reliability. Both sides approach the same problem with different perspectives. “Classic” IT puts security first, reliability, second. OT, just the opposite. It takes knowledge of both, and a dash of diplomacy, to strike the right balance. We strongly recommend joint efforts with a person from each side (OT and IT) working TOGETHER and reporting to someone who can act as arbitor as necessary. The arbitor role is suitable for using a consultant.
“Lack of insecurity” – we are not sure what this question means. If it means overconfidence in existing measures, the answer is a resounding yes. Even air-gapping can be compromised via an insider threat, and typically, air gapped networks other than military are poorly defended against insider threats. (NAC helps a great deal here.)
“Investing in features … “. Again, we are not sure what this means. We need a concrete example. However, we can only stress that most businesses with OT networks are grossly UNDERINVESTED in cyber security. Their IT networks are likely to be better defended than their OT networks. However, with the irresistable trend in IT – OT convergence, it is CRUCIAL that OT networks be better defended. Or they will be hacked. Not if – but when.
Q9. *Is it due to insecurity?
Answer by Arthur J. Carp, Quantalytics, Inc.
See “lack of insecurity, above. If it means that people are too scared to try to take corrective actions, this is true. Bad decisions can be career breakers for people. But so can no decision, and then an incursion occurs, and careers are destroyed. The first step is to start a dialog between IT (Cyber Security) and OT. If necessary, for Cyber Security, go outside your company for a consultant if your company does not have adequate (in OT’s opinion) IT Cyber Security. You must build communications and trust across the 2 disciplines. They hold opposite views on security vs. reliablity. However, a middle ground, can, and must be reached between the two, and OT networks MUST be better secured than currently, where unsurprisingly, most are not secure at all, including against insider threats. (E.G. Disgruntled employee.)
Q10. The greater the number of tiers in defense in depth the more folks are required to monitor and take action.
Answer by Arthur J. Carp, Quantalytics, Inc.
This is an incorrect conclusion. Properly configured, the same people are better and sooner informed of a problem via more layers of defense (“defense-in-depth”). For example, a honeypot alert can confirm and validate and IDS (Intrusion Detection System) warning that a hacker has entered a network and is reconning it via “living off the land”. Without this confirmation, there is a real risk the IDS warning will be treated as a false positive, or even missed amid a deluge of warnings. One way to throw off defense is to trigger a flood of false alarms (false flags) to hide the real activity.
In conclusion. We (Quantalytics, Inc.) also recommend that OT people read military strategy textbooks. We are in the midst of a war, and the bullets and bombs are ethernet packets. You may quote me. I assure you, this is not overdramatization. The stakes are large and growing.
Session is available on demand now. Log in and watch it here.
Deep further into this topic with a cyber-readiness guide.
Richard Ku, Trend Micro
Richard Ku had been working in the cyber security industry and with Trend Micro for more than 28 years, working on a number of leading roles from individual contributor to management position. Richard has extensive experience and knowledge working and developing security product and services for multiple segments of the market; from consumer to small business and to some of the world largest enterprise customer. Currently, Richard is responsible for the sales and market development of Trend Micro Industrial IoT (OT) Security business in the Americas.
Arthur J. Carp, Quantalytics, Inc.
As the Founder and CEO of Quantalytics, Inc., Arthur has full responsibility for the product planning, development, technical implementation, manufacturing and testing of the Quantalytics Network Security Appliances product line. His responsibilities include strategic planning for new product rollout, development of new technologies, oversight of outside creative development and implementation of all technology efforts. This also includes leading a talented team of specialized cyber scientists to create high value cyber defense appliances in addition to be a “hands-on” development practitioner.
To ensure that Quantalytics’ product development is closely aligned with current and future client needs, Arthur has responsibility for the product roadmap.
Arthur is a graduate of The Massachusetts Institute of Technology (MIT) with Degrees in Mathematics (S.B.) and Chemistry (S.B.). He has lead Quantalytics since its founding over 30 years ago by constantly looking at applying the most advanced technologies available to business problems.



