OT:ICEFALL: Addressing Operational Technology Equipment Flaws with Zero-Trust Controls
A new report on Operational Technology (OT) equipment flaws from automated cybersecurity software company Forescout outlines the alarming state of OT security. The report titled OT:ICEFALL was crafted by researchers at the company’s Vedere lab. It breaks down 56 vulnerabilities affecting 26 devices from 10 vendors in OT.
The findings sound an already blaring alarm about how many OT systems and components are insecure-by-design. While there has been a concerted effort to harden OT security over the last decade, most OT still in use today was not designed with any security features in mind. Since industrial equipment is built to last for decades in service, connecting technology still in use today to a network or the outside world was not even a thought when it was designed and implemented. And now that connectivity is becoming a necessity, we’re playing catch-up when it comes to security.
Therefore, most OT is considered “insecure-by-design.” And by extension of the fact that security in OT has been an afterthought, vulnerabilities have historically not been assigned a Common Vulnerabilities and Exposure (CVE) classification. As Forescout points out in its report, the lack of any standard mechanism for tracking and giving visibility to vulnerabilities in OT makes it very difficult for operators to find issues in their systems, and for vendors to fix them.
Forescout’s report is an important resource because it compiles vulnerabilities from major OT vendors in one place. One of the most interesting things the company found by digging in further is that 74% of the affected product families have some form of security certification – which raises serious concerns about the state of OT security certifications. As the research says, “most issues we report should be discovered relatively quickly during in-depth vulnerability discovery.”
Another interesting component of the report is how it divided the vulnerabilities into different categories for the type of risk they enable. More than one-third of the vulnerabilities identified in the report (38%) allow for the compromise of credentials, which is by far the biggest threat. Firmware manipulation is the second biggest threat (21%), followed by remote code execution (14%). Other threats include configuration manipulation, denial of service, authentication bypass, logic manipulation, and file manipulation, which are all potential risks from less than 10% of the identified vulnerabilities.
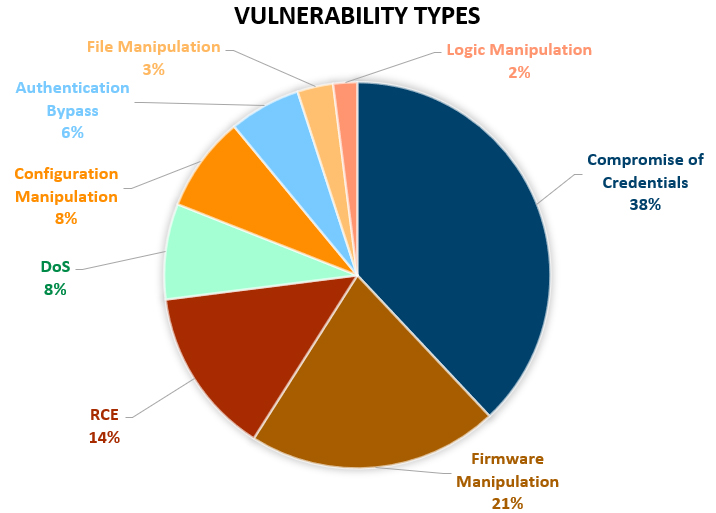
Source: Forescout OT:ICEFALL Research Report, July 2022
The potential negative outcomes due to Insecure-by-design OT could be catastrophic. If attackers get into a gas pipeline, water treatment facility, or power plant, human lives are at risk. This report shows how easily hackers can manipulate firmware, logic and files once they gain access to a network IF the company doesn’t have proper security models in place. In today’s age, companies need remote user access, but enabling it immediately increases their attack surface. So where do we go from here?
The industry must recognize that these vulnerabilities will not be resolved by simply patching the impacted systems. They are architectural in nature and can only be remitted by re-designing the system and completely replacing it, which can take 5-10 years. The other option is a built for OT, zero-trust user access platform that can be deployed to protect these vulnerable systems immediately.
To address the lack of secure-by-design industrial control systems, enterprises must implement a more universal zero-trust architecture to properly protect against these security flaws expeditiously. These zero-trust controls can include protocol isolation to immediately and drastically reduce the attack surface, strong multi-factor authentication to remove move weak authentication methods, moderated file transfer and moderated access to critical assets to provide added site level controls, and user access monitoring and session recording to ensure proper operations to conduct deeper forensics when threats emerge.
We can either continue to have the stress and consequences of systemic risk to public and economic safety, or we can implement modern and secure authentication and authorization zero-trust controls to address it immediately.
Originally this article was published here.



