What You Need to Know About Securing 5G Networks and Communication
|
Getting your Trinity Audio player ready...
|
We live in a hyper-connected world. The prevalence of 5G networks has made it easier for devices to connect in more ways, leading to an explosion of IoT devices. In turn, this explosion of IoT devices has led to the creation of even more 5G networks, both public and private.
Now, we can easily connect to anyone and anything, and this always-present connection has become critical to almost every aspect of our lives. It’s also become a prime target for cyberattacks. That’s because every time you add a new device or piece of infrastructure, you also add a point of entry for attack – and as the number of connected devices explodes, this creates new security considerations.
Specifically, owners of public and private networks must prioritize end-to-end security for the entire network and all devices connected to it. But with the growing demands of new connected devices and evolving standards, this isn’t always straightforward.
So what do 5G providers need to know? Below, I dive into the state of security in 5G and IoT, security standards, and how PKI and other security solutions can help both public and private 5G providers meet current and future security needs.
The state of security in 5G and IoT
IoT devices have exploded over the past several years, and this growth shows no signs of slowing down. And all of these devices have one thing in common: Remote connectivity via a public 4G or 5G network, or, increasingly, a private 5G network.
This explosion of connected devices creates an expanded attack surface, since the entire network is only as secure as its weakest link. Specifically, just because a network is secure, any devices attached to it that are not secure in how they communicate or receive updates create a breach opportunity.
As a result, it’s essential that every device has an identity and each identity is managed. This might sound daunting, but it’s not as complex as it seems at first – it goes back to the building blocks of PKI. Much of the security industry has a handle on running PKI for enterprise networks in their organization (think laptops, mobile devices, and so on). Therefore, security teams are also enabled to do PKI for these smart devices — it’s the same approach for a different endpoint.
Ultimately this means security can’t sit in a single spot in the manufacturing chain. Rather, it must be present at every step of the way, because what happens at one level – let’s say with the silicon vendor that manufactures chips or the OEM who puts everything together – impacts everything that follows – whether that’s for the service provider or end user.
Security standards for 5G networks
We’re starting to see security standards emerge around remote connectivity, whether that’s by a consortium (3GPP TS 33.310 for x.509 certificates), federally (FCC part 96 for private 5G networks), or regionally (ITU-R M.2083, requirements for international 5G). All of these emerging standards vary, which results in broad requirements to consider during security design conversations.Let’s look at how this plays out for two common architectures for 5G cellular networks:
Backhaul security using X.509
Backhaul security using X.509 is the bread and butter of cellular networks. User equipment like phones, tablets, IoT devices, or anything else on the public cellular network uses base station eNodeB vendor certificates, while network devices like the mobile backhaul, the transport, or core network functions use IPSEC with 3GPPP on the backhaul to encrypt traffic going from base station to security gateways. Having IPSEC everywhere on the backhaul is essential for maintaining a zero-trust approach to security in which nothing is trusted, and everything must be verified.
In general, it’s important to have a multi-layered approach to security in these scenarios. For example, you can use TLS for application security, SSH certificates for OSS functions and network management, and SIM cards for user equipment (with thousands or millions of devices, the new IoT SAFE standard can help manage all of these SIMs).
Private 5G networks
A private cellular network, or private 5G network, is exciting because it allows you to stand up your own dedicated network without the time-consuming and expensive bidding process associated with getting a license for a public cellular network from the FCC.
Private 5G also offers a highly robust IoT environment since it’s not as susceptible to interference as WiFi, and it supports a higher density of devices – think a factory floor full of robots, surveillance cameras, tablets, and more, all running on the private 5G network.
Once again, a multi-layered approach is essential, with X.509 certificates, IoT SAFE for SIM management, TLS certificates, SSH certificates, and IPSEC between the CBSD and EPC. Importantly, even though most CBSDs or private LTE access points will come with encryption certificates, it’s a good practice to rotate those vendor certificates out with certificates from your own PKI for better control over all lifecycle management activities.
Evolving use cases for PKI in 5G networks
As 5G continues to expand, the use cases for PKI in securing 5G networks do too. Here’s a look at some of the most promising approaches we’re seeing today:
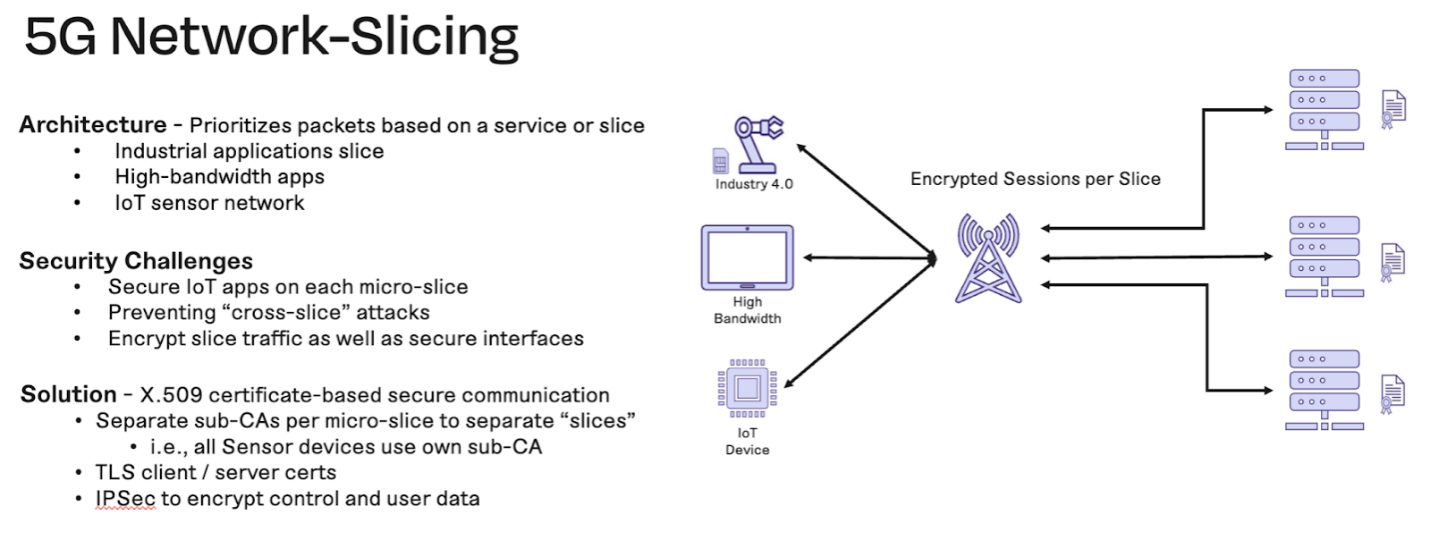
5G network slicing
5G micro-slicing separates the network into different slices (aka services). This is particularly useful in IoT, where you might have an industrial application slice, a high-bandwidth application slice, a sensor network slice, and so on. Essentially, this approach allows you to divide each application by service to optimize traffic and avoid having high-bandwidth apps overrun your data. Of course, it’s important to secure each slice by encrypting traffic for each one using X.509 certificates, TLS, and IPSEC.
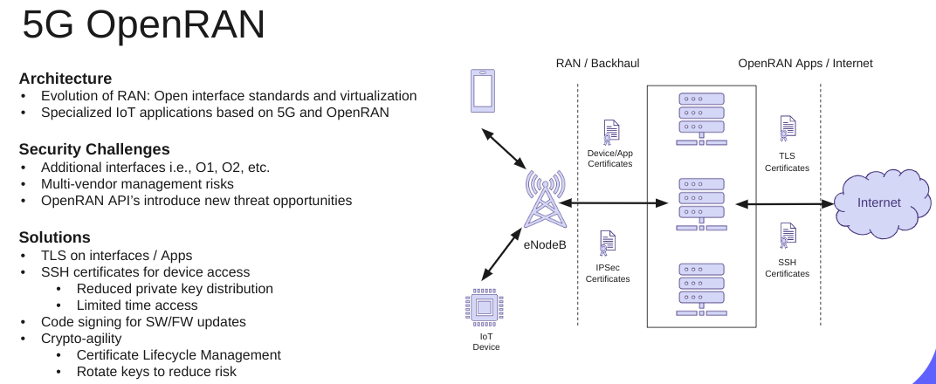
5G OpenRAN
Another exciting approach is 5G OpenRAN, which makes proprietary hardware and software open source so that you can create your own custom applications. For example, instead of spending the time and money to run fiber and a cable to put an application in a data center, you can rely on the OpenRAN standard to put in a device with a 5G transceiver and use that signal to run updates, achieving the same outcome but with zero day provisioning. OpenRAN does bring in extra layers of complexity with security since it has multiple interfaces for management and multiple vendors involved. Therefore, it requires TLS, SSH, code signing for updates, and crypto-agility for certificate lifecycle management.
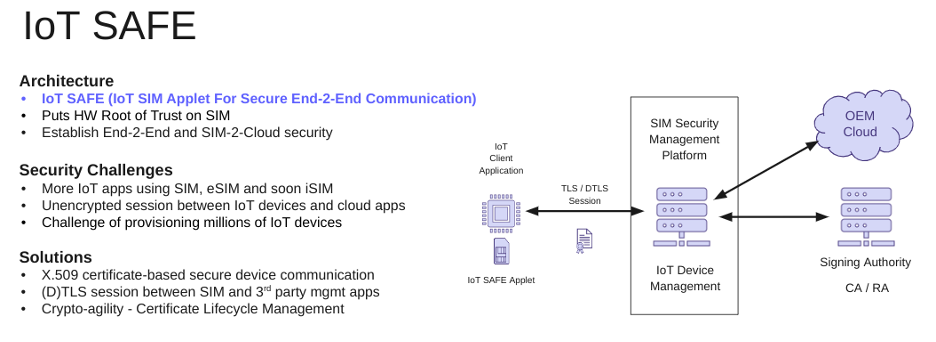
IoT SAFE
With billions of IoT devices (and counting), we’re seeing more and more SIM cards, and each one requires management – which can become quite challenging at scale (just think about manually rotating SIM cards, blocking old ones, etc., and it’s enough to make your head spin). With IoT SAFE, you can put the hardware root of trust on a SIM, which enables you to use PKI to dynamically manage those SIM cards. This approach requires X.509 certificates for secure communications, TLS sessions between the SIM and third-party management apps or your cloud provider, as well as crypto-agility for ongoing certificate lifecycle management.
The future of security for 5G networks and communications
Security is no longer optional or a key differentiator: it’s expected. And it must be able to scale alongside the explosion of devices operating on 5G networks.This means 5G providers must prioritize end-to-end security through PKI as described in the approaches here. And as we well know, everything can – and will – change fast, which requires crypto-agility to keep up with an ever-evolving landscape.
About the author
 This article was written by Granville Dillon, Senior IoT Solutions Architect, Keyfactor.
This article was written by Granville Dillon, Senior IoT Solutions Architect, Keyfactor.



