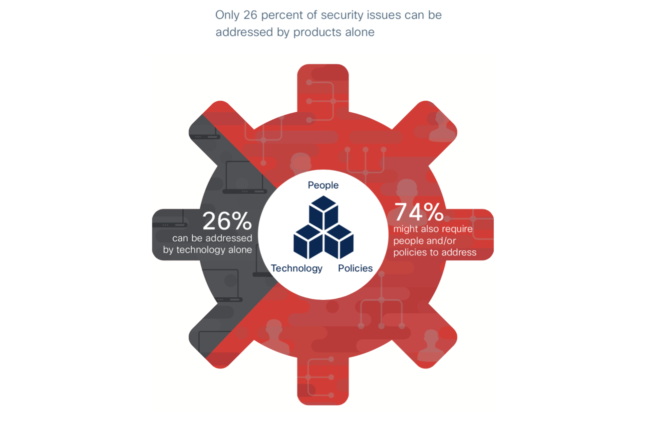
Cisco’s cybersecurity recommendations/solutions for manufacturing
Hannover Messe has been a great success for many companies this year. One of the topics we had on our radar at this event was cybersecurity. As Oliver Tuszic, VP and General Manager of Sales at Cisco, Germany, said, it is imperative that in the process of digital transformation companies feel secure. At this point, there is not enough trust in digitalization because people don’t understand what cybercrime means for them. The good news is that defenders can see what’s on the horizon. Many clues are out there before an attack hits.
According to a recent Cisco 2018 annual cybersecurity report, adversaries and nation-state actors already have the expertise and tools necessary to take down critical infrastructure and systems and cripple entire regions. But when news surfaces about disruptive and destructive cyber attacks, some security professionals might initially think that their companies/market/technology environment wasn’t a target, so, they probably not at risk. In this situation, defenders fail to recognize the speed and scale at which adversaries are amassing and refining their cyber weaponry.
For years, Cisco has been warning defenders about escalating cybercriminal activity around the globe. In their latest annual cybersecurity report, the company present data and analysis from Cisco threat researchers and several of their technology partners about attacker behavior observed over the past 12 to 18 months. Many of the topics examined in the report align with three general themes. As our focus is on industrial cybersecurity, we will present a few stats from the report related to ICS security.
Threat researchers with TrapX, a Cisco’s partner, recently conducted investigations into several cyber attacks that targeted customers’ ICS to help highlight unexpected problems with ICS cyber defense. Two of the incidents, described in the report, took place in 2017 and remain under investigation.
Target 1: Large international water treatment and waste processing company
Attackers used the company’s demilitarized zone (DMZ) server as a pivot point to compromise the internal network. The security operations team received alerts from deception security technology embedded in the network DMZ. This physical or logical subnetwork bridges internal networks from untrusted networks, such as the Internet, protecting other internal infrastructure. The investigation found that:
- The DMZ server was breached due to a misconfiguration that allowed RDP connections.
- The server was breached and controlled from several IPs, which were connected to political hacktivists hostile to the plant.
- The attackers were able to launch multiple significant attacks against several of the company’s other plants from the compromised internal network.
To read about the other incident (Target: Power plant) and see Cisco’s recommendations, download the report. For additional case studies, see the TrapX Security research paper, Anatomy of an Attack: Industrial Control Systems Under Siege.
According to Cisco 2018 Security Capabilities Benchmark Study, more OT and IoT attacks on the horizon in 2018.

The same study shows that 53% of attacks result in damages of $500 000 or more. Read research and find out more about:
- ICS cybersecurity challenges and obstacles
- Complexity created by security vendors in orchestration
- The most likely industries to be affected by security breaches
- The investment in technology expectations
Speaking about cybersecurity, you might also want to know more about Industrial Network Director Security.
To learn more about Cisco’s approach to ICS security, visit https://blogs.cisco.com/manufacturing/ib-security-in-mfg
Also, in case you missed Cisco at Hannover Messe 2018, you can find more resources related to smart manufacturing here and here.
This article is part of Cisco’s paid campaign with us.
Carolina Rudinschi, PhD, author of a Digital Media Book, brings a wealth of experience in Public Relations, Research, Journalism and Social Media.