The IoT world is a big world that everybody is talking about. IoT products nowadays come in different forms — some are labelled as IoT, but in fact they represent only a small portion of what an IoT product really entails. A fully fledged IoT project not only requires programming and hardware expertise but also expertise on a broad range of domains from energy to smart home and even automotive.
The purpose of this article is to highlight the significant differences among the Internet of Things (IoT) and Industrial Internet of Things (IIoT), and while walking through the listed considerations, the reader will have the chance to learn about their ecosystems and the particularities of their applications. Moreover, the gaps in the standardization of the technologies related to the IoT are presented along with the current initiatives from various institutions for mitigating these gaps.
Common Ground
Before talking about the differences between the IoT and IIoT, let’s look first at the similarities of the two. Both have the same fundamental layer on top of which they are built. With IIoT being a subset of the larger IoT, they automatically share common technologies like sensors, cloud platforms, connectivity and analytics.
Another similarity constitutes the domains for which their application is designed, as well as the standards and regulations they have to conform to in order for them to be successful and commercially available.
The IoT Landscape
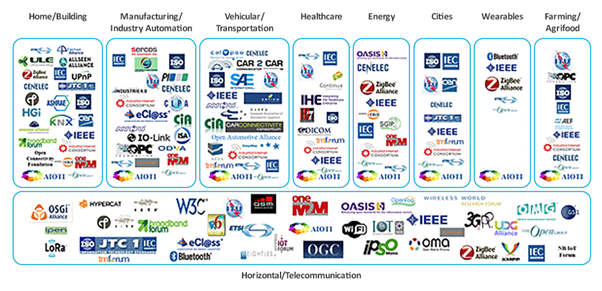
Figure 1:The IoT Standards Landscape (ETSI, 2017)
The figure above summarizes the current situation in the IoT world with respect to the standards and the application domains in which these types of products are used. The landscape is valid for both IoT and IIoT products. Both of them are used in various applications which extend from home automation up to farming and agriculture — vertically. On the horizontal, we can find common telecommunication technologies that are used in all the presented application domains. As we can infer from the figure, the application domains are densely populated by several SDOs (standard developing organizations) and industrial or public alliances.
The image shows two very critical drawbacks for the future IoT standards. Firstly, there are too many players on the field and secondly, the SDOs are mostly independent and there is little reuse between them, and to some extent they are competitors in the race to be the first and most relevant in the market.
The Big Gaps
The standard developing organizations (SDOs) are part of the European Alliance of IoT Innovation (AIOTI). More information about the alliance can be found on their website https://aioti.eu/.
Based on the IoT landscape image, ETSI (a European Standards Organization — SDO) published an interesting analysis where they identified six main gaps in the IoT:
1. Duplication of IoT architectures and models
2. A large number of communication protocols address heterogeneous types of communication requirements
3. Data models are developed on a proprietary basis and mostly specific to the vertical domains to which they apply
4. Processing rules and decision-making processes under the reception of sensor data lack in harmonization
5. Security and privacy are addressed on an isolated basis for some of the applications
6. Ease of use and maintenance after purchase would require a more global approach
The IoT Technology Stack
Prior to diving into the details, it is important to understand that not all connected devices are IoT or IIoT. In this section, we will understand more about the IoT ecosystem and its fundamental components.
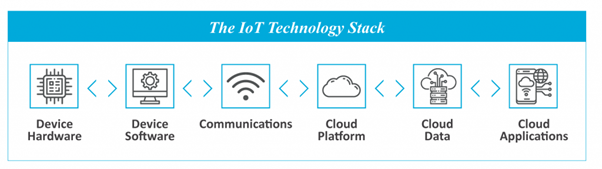
Figure 2: The IoT Technology Stack
The technology basis for any IoT application — whether intended for the consumer or for industry — is the same, and can be abstracted as shown in the figure. Therefore, building a product from scratch and calling it an IoT product requires expertise in six different domains (Dunkels, 2019):
- Device Hardware
- Device Software
- Communications
- Cloud Platform
- Cloud Data
- Cloud Application
Additionally, the security aspect of each of these components shouldn’t be forgotten. In the interest of a simplified representation, this aspect is not accounted here, as this would require its own dedicated chapter.
Device Hardware
When we imagine an IoT product, a physical device is automatically brought to mind. This can vary from the extremely simple, say an electronic device sporting some colorful LEDs, to the highly complex, like a device sensing different physical properties and engaging in so-called edge computing. The main requirement when building such products is to incorporate communication technology that allows the device to communicate with other devices or to be connected to the internet.
Device Software
The software component of any microcontroller-based hardware is called firmware. The firmware is the piece of logic any IoT product needs to operate and perform the desired workload. Find out more about selecting the right microcontroller for your IoT project.
Communications
The communication is usually realised by connecting to other devices and ultimately to a master gateway, or by connecting directly to the internet using different technologies such as Bluetooth, WiFi or any other standard communication protocol.
Cloud Platform
Any IoT product requires a backend solution where the data is collected, filtered and processed. Some of the most commonly used cloud platforms today are shown in the picture below. More information about the leading cloud platforms can be taken from (*um, 2019).
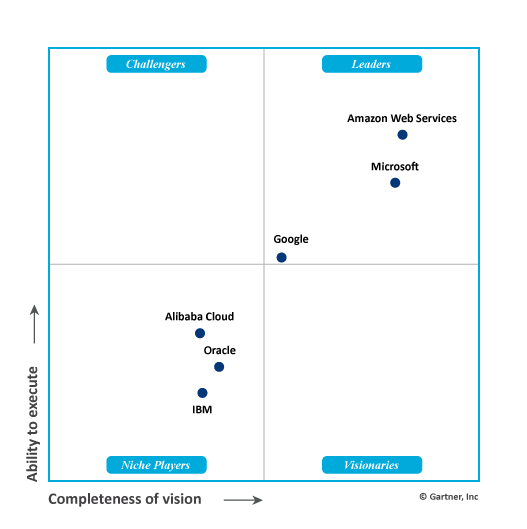
Figure 3: The Magic Quadrant for Cloud Infrastructure (Gartner, 2020)
Cloud Data
This component is theoretically optional in an IoT application; nonetheless, most of the products today incorporate an intelligence for differentiating from other products. Usually this is perceived as being the most valuable asset of any modern IoT product; therefore, expertise in areas like Machine Learning and Data Science are highly required.
Cloud Applications
Just as with the Cloud Data, this component is optional, as not all IoT applications offer a GUI-based visualization to the customer. In case this is required, the cloud application must be capable of showing the data collected from the device hardware in the form of a mobile or web application.
Ten Differences between IoT and IIoT
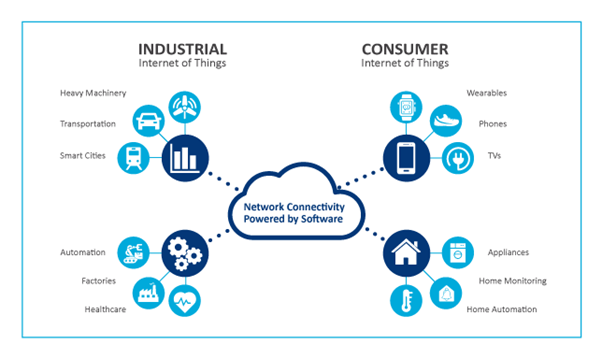
Figure 4: The IoT and IIoT application domains (Bureau, 2017)
While many people assume functionality distinguishes the IoT from the IIoT, the reality is not that simple. Although the IoT and IIoT share common technologies, the similarities end there.
First, to start with the definition of the two. The term IoT, Internet of Things, is often used to refer to ubiquitous, consumer-oriented IoT products.
The IIoT, on the other hand, stands for Industrial Internet of Things, and is a subset of the larger IoT, focusing on the specialised requirements of industrial applications such as manufacturing, oil and gas, and utilities. IIoT is a collective term that describes the connection of machines and production plants.
According to (Ehrenreich, 2018) and (Chan, 2018) the parameters that differentiate the IoT from the industrial IoT include:
· Security
· Interoperability
· Scalability
· Precision
· Programmability
· Low Latency
· Reliability
· Resilience
· Automation
· Serviceability
Security
Any kind of IoT solution requires security, but industrial IoT solutions require more robust measures. Resolving security on a merely superficial level can have a disastrous outcome for a high-volume manufacturing process, resulting in lost production costing huge amounts of money. Another outcome of incorrect action in the control process can put the system into an unstable and unsafe condition. Therefore, IIoT solutions incorporate sophisticated security measures, from secure and resilient system architectures, specialised chipsets, encryption and authentication threat detection to management processes.
On the other side, operation safety is not necessarily an issue in an IoT ecosystem as these systems do not handle industrial processes. Therefore, no serious safety incident can happen if a wrong decision is made.
Interoperability
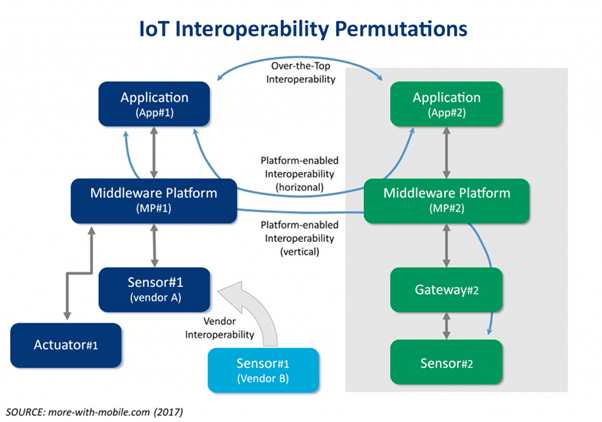
Figure 5: The IoT Interoperability Permutations (more-with-mobile.com, 2017)
Usually, industrial IoT applications must co-exist in environments with significant amounts of legacy operations technologies (OT). These legacy OT don’t go away so fast; therefore, industrial IoT solutions must integrate, support various protocols and data sets, and work reliably with these systems.
Scalability
The term industrial suggests large-scale networks supporting a high amount of devices in the order of tens of thousands (or more). These devices can be controllers, robots or large machinery and IoT solutions deployed into these networks must scale seamlessly and support hundreds of thousands of sensors and devices as well as existing non-IoT devices.
Precision
Figure 6: Example for increasing the positioning accuracy (Fahem Zafari, 2019)
Industrial operations require higher levels of accuracy. Automated, high-speed machinery is synchronized to a matter of milliseconds. Therefore, the quality must be assured for such systems. Any small variation in the operation of such high-volume manufacturing processes must be corrected right away. Otherwise, this can result in lost efficiency and downtimes which can affect the revenue considerably.
Programmability
The programming and reconfiguration of industrial machines is frequently performed. This can be done remotely, on site or in the field and the industrial IoT solutions supporting industrial and manufacturing processes must provide reliable flexibility and adaptability.
Low Latency
Complementary to precision and accuracy is the requirement for low latency in industrial applications. Anomalies must be quickly detected and corrective actions must be applied in near-real time.
Reliability
Industrial products are usually designed to operate for twenty to thirty years before a scale replacement is performed. With these strict requirements, like operating in harsh environments, sometimes subject to extreme cold, heat, high vibration, pressure and hazardous conditions, the IIoT applications must assure reliable operability and high availability.
A wrong action can put people’s lives at risk.
Remember that the “reliability” aspect is part of the SRP triad: Safety, Reliability and Productivity.
Resilience
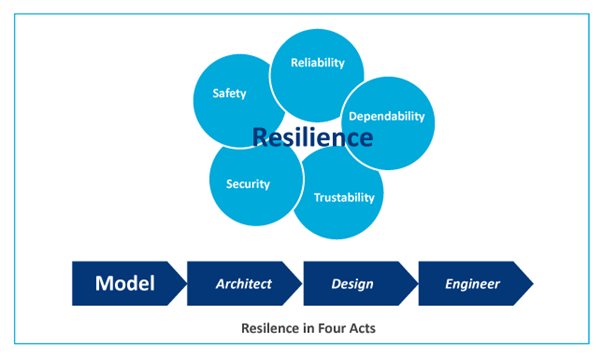
Figure 7: The Resilience Model in Four Acts (Delic, 2016)
Breakdowns in one part of the system are not unusual in such highly scaled industrial applications; therefore, the applications must be designed with resilience in mind. To compensate for such faults in the system, the IoT system architectures must be designed to always satisfactorily complete their processes and operations.
Automation
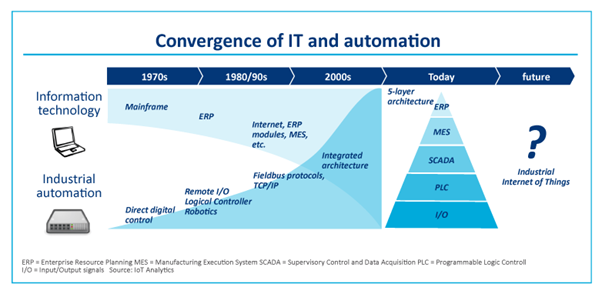
Figure 8: The Short History of Automation in IT (Lueth, 2015)
Most of the industrial applications are highly automated from the bottom to the top, with limited or absolutely no human intervention. Such IoT solutions are required to support a range of autonomous actions. In order to ensure this, applications do incorporate intelligence into the edge devices, or deep learning capabilities in the system design.
Serviceability
IoT solutions operating in industrial environments must be serviceable in order to sustain the levels of performance required. This can extend from swapping out sensors and updating firmware to configuring gateways and servers — the ability to maintain industrial IoT solutions over their entire lifecycle is an essential requirement.
Outlook
Having learned about the technological fundamentals as well as about the differences between the IoT and IIoT, it is now easier to better assess a product which is about to be developed or to resurrect a legacy product which must be in conformity with the 2020s.
Anyone considering to develop a new IoT/IIoT ecosystem should evaluate both of these common and distinct characteristics and decide together with the customer on the best suitable architecture without compromising the intention of the application.
One of the key takeaways is that when building industrial IoT products, one has to focus on the real needs and values of a properly designed cloud data-based architecture with a special focus on the safety, reliability and productivity aspects. Clodless IIoT: is this possible?
References
*um. (2019). Public cloud providers overview: AWS, Azure and Google. Von https://www.unbelievable-machine.com/en/en-public-cloud-providers-overview/ abgerufen
Bureau, E. T. (2017). Consumer IoT to be Bigger Market than Industrial IoT. Von https://www.eletimes.com/consumer-iot-bigger-market-industrial-iotabgerufen
Chan, B. (2018). Ten ways IoT differs from IIoT. Von https://www.iiot-world.com/industrial-iot/connected-industry/ten-ways-iot-differs-from-iiot/ abgerufen
Delic, K. A. (2016). On Resilience of IoT Systems. Von https://www.researchgate.net/figure/Resilience-Studies-and-Acts_fig1_294105970 abgerufen
Dunkels, A. (2019). Technical Skills Needed For Professional IoT Projects. Von https://www.thingsquare.com/blog/articles/developer-profiles-for-successful-iot-projects/ abgerufen
Ehrenreich, D. (2018). IoT vs IIoT differences you must know. Von https://www.iiot-world.com/industrial-iot/connected-industry/iot-vs-iiot-differences-you-must-know/ abgerufen
ETSI. (2017). IoT Standards Landscape. Von https://aioti.eu/wp-content/uploads/2019/10/AIOTI-WG3-SDOs-Alliance-Landscape-IoT-LSP-standrad-framework-R2.9-Published.pdf abgerufen
Faheem Zafari, A. G. (2019). A Survey of Indoor Localization Systems and Technologies. Von https://arxiv.org/pdf/1709.01015.pdf abgerufen
Gartner. (2020). Magic Quadrant for Cloud Infrastructure and Platform Services. Von https://www.gartner.com/doc/reprints?id=1-1ZDZDMTF&ct=200703&st=sb abgerufen
Lueth, K. L. (2015). Will the Industrial Internet Disrupt the Smart Factory of the Future. Von https://iot-analytics.com/industrial-internet-disrupt-smart-factory/ abgerufen
more-with-mobile.com. (2017). Making Sense of IoT Interoperability. Von https://internetofthingsagenda.techtarget.com/blog/IoT-Agenda/Making-sense-of-IoT-interoperability abgerufen



