8 technologies that an organization can adopt to help address its cybersecurity challenges
In defining policies and procedures around the implementation and management of security controls in an enterprise environment, the organization is advised to adopt a cybersecurity framework to overcome challenges. This is a series of documented processes that can provide the baseline best practices to help the organization plan, design and deploy security controls on cyberthreats.
How to address cybersecurity challenges
Pertinent standards include the NIST 800-53 cybersecurity framework and ISO/IEC 27000 series13 for information security, and IEC 62443 for control systems. A security program typically includes the following core components across both the IT and OT environments: Identify, Prevent, Detect, Respond, Recover and Predict. Within each phase, there are specific processes and activities that the organization should follow to ensure the successful execution of the entire framework.
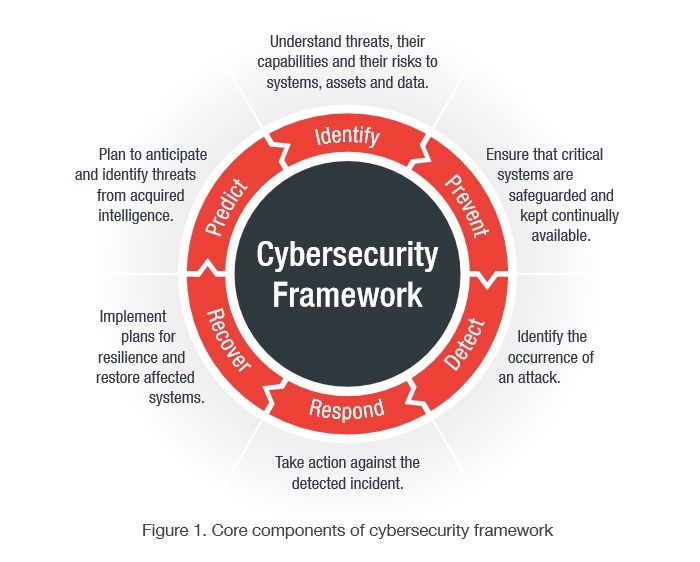
Technologies to consider when addressing cybersecurity challenges
For IIoT to provide its projected benefits in the IT/OT environment, security concerns associated with its implementation must be addressed first using available technologies and capabilities.
Doing so, of course, entails development of secure and authenticated process sensors. There’s also the need for a system to detect malware and other ICS network anomalies. In line with this, process anomaly detection could be put in place and correlated with ICS network anomaly detection to understand the process system impact of network issues.
Next-generation firewalls also need to be installed to properly segment IIoT networks and provide predictive threat analysis. As well, integrated configuration management systems are necessary for the integration of security information and event management (SIEM) with ICS configuration management.
There are many other available technologies and capabilities that an organization can adopt to help address its cybersecurity challenges in the new converged environment.
Technologies to adopt to help address cybersecurity challenges
- Next-generation IT and OT host-based intrusion prevention and detection systems, including all IoT and IIoT protocols
- Anti-malware and ransomware protection for both IT and OT environments
- Whitelisting for both IT and OT environments
- Network sandboxing technology that can analyze and monitor for vulnerabilities and threats on the different types of IoT protocols without affecting the operational process
- Threat analytics and correlation solutions that can collect information across different environments to help the management team make decisions
- Encryption technologies for providing authentication and verification, which are a must across all IoT devices and control systems
- Technology for managing versions of devices, control systems, patches and the like across both IT and OT environments to ensure the organization understands the risk across both of these environments (includes management of version, status, last update, control system version, patch version, etc.)
- Security capabilities in the form of software development kits (SDKs) or application programming interfaces (APIs) that can be directly integrated into devices. More about the Three Types of Security in IoT
See other tips on how to protect your network from malware attacks.
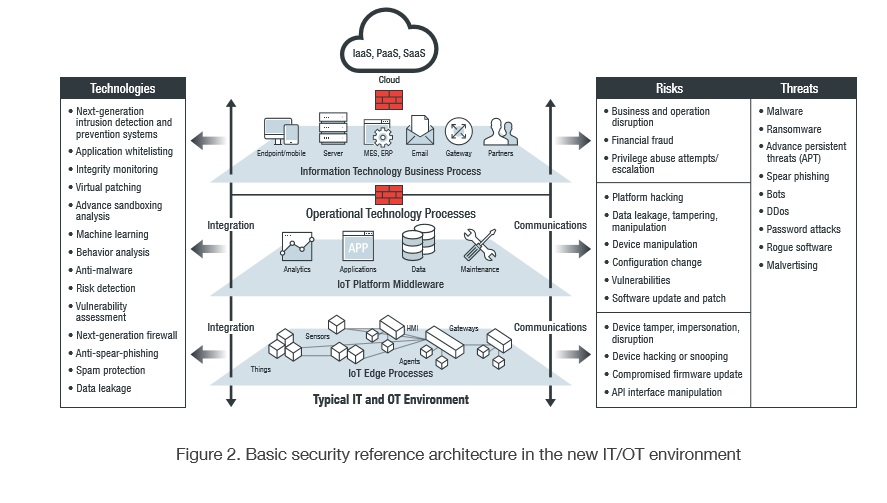
Deploying security controls across the entire organization also requires a good understanding of the network architecture across both the IT and OT environments. By understanding the network architecture, the organization can better analyze where the threat is coming from and what controls need to be applied in the network architecture to address the threat. Below is a network diagram showing the architecture of the IT and OT environments and where to best deploy security controls to ensure a defense-in-depth protection strategy. By applying security controls and policies in all layers of the network architecture, the organization will make it more difficult for attacks to succeed.
More information about security technologies
To learn more about IT/OT Convergence and Cybersecurity, Security Challenges for IIoT, Best Practices for the IT/OT Environment, Cybersecurity Framework, Technologies to Consider and how to Choose a Security Vendor, download this free whitepaper.
This is an excerpt from the “Integrating Security Into the IoT Strategy in the New Converged Environment” whitepaper, written by Richard Ku & Joseph Weiss.
Richard Ku has over 23+ years of hands-on experience working in the hi-tech and security industry in a number of leading roles, as individual contributor and management. Currently served as Sr. Vice President of Product and Services Management for Trend Micro Enterprise and Small Business Foundation Security Product and Services.
Joe Weiss, PE, CISM, CRISC, ISA Fellow, IEEE Senior Member, MD ISA99, is an industry expert on control systems and electronic security of control systems, with more than 40 years of experience in the energy industry. Mr. Weiss spent more than 14 years at the Electric Power Research Institute (EPRI) where he led a variety of programs including the Nuclear Plant Instrumentation and Diagnostics Program, the Fossil Plant Instrumentation & Controls Program, the Y2K Embedded Systems Program and, the cyber security for digital control systems.
Sorry, the comment form is closed at this time.





Pingback: Cybersec News – January 2018 – My (Yet Another) Cybersecurity Blog
Pingback: 8 technologies that an organization can adopt to help address its cybersecurity challenges - Secure Signal NYC