Critical Infrastructure and ICS Security Remain a Network Segmentation Problem
Companies in every industry are developing and implementing connected industrial control applications as strategic digital business initiatives. However, the risks of security breaches and the subsequent impacts to consumer privacy and now personal safety are limiting the delivery of secure and resilient services, that are based on these connected applications. Many company’s networks remain disconnected due to the fundamental problem that these network architectures where built on an older, non-secure tapestry of legacy sensors, controllers and serial communications buses which are vulnerable to attacks regardless, if they are connected or not (Stuxnet).
The Role of ICS Network Security
In established industrial nations, the Industrial Control Systems (ICS), their actuators and serial communications buses (MODBUS, PROFINET, etc.) are the new threat vector for attacking Critical Infrastructure, Industrial and Building Automation applications. There is significantly less cost and technical hurdles involved in attacking these systems than those of a new cloud solution. And unfortunately, these attacks offer the same or worse outcomes as large-scale distributed IT attacks.
For any company trying to protect against these threat vectors, there is an additive operational cost to securing these types of brownfield, or installed, systems. The actuators, sensors, and gateways integrated into these legacy networks were not created with security as a priority. These devices exist in Operations Technology Levels 0, 1 and 2 of the stack, from the Frost & Sullivan table below:
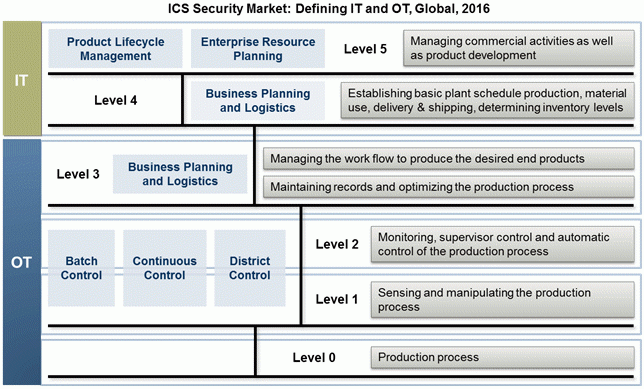
Many believe using artificial intelligence (AI) in the cloud will solve the ICS security issue; however, AI systems do not have data from Level 0 and Level 1 or even Level 2 of the stack. Furthermore, if the devices at Levels 0 through 2 remain unchecked, or their identity unauthenticated, the data being used for the algorithms can be corrupted and provide incorrect baselines. Also, the amount of data being generated by these devices is so significant that it is likely cost prohibitive to store in a cloud solution.
This lack of authenticated identity for devices coupled with the low rate of capital expenditures in these markets is the real problem with critical infrastructure systems. This also limits the adoption of further connected intelligent devices, today and in the foreseeable future. Further complicating this problem is the convergence of the operational networks with IT networks. More about Values and Challenges of SCADA Systems for Outside-the-Fence Applications
Solution: ICS Network Segmentation
The best solution is for firms to segment and segregate their monitoring, communication and control networks using an identity-based approach to control network communications. Using authenticated identities provides strong and adaptable access policies to control who can connect to the network, and which assets and data they are able to see. As we connect more intelligent devices to existing or new cyber physical controls, or connect monitoring systems into critical infrastructure applications, we continue to increase the risk of security breaches and the loss of control of our devices and our privacy. More importantly this offers an adversary the opportunity to damage property, affect business services that negatively impact revenues, cause production and service downtimes and most importantly, potentially take human lives.
ICS and SCADA systems control the operation of systems which, if tampered with, can produce disastrous outcomes, such as turning on a branch of the power grid in a city or factory that is supposedly offline when a worker is attempting a repair or making a new connection. From a monetary perspective, when TSMC, one of the most secure and sophisticated factories in the world, was hacked this year, the firm lost over $171M from downtime of their production lines, per CNN’s coverage.
Our solutions are capable of brownfield deployments in legacy networks to segment and segregate active ICS and SCADA systems. Further, we can assist our customers in achieving the US-CERT recommendations for improving the security of network infrastructure devices by providing a topology independent approach to network segmentation and segregation. Non-interactive identity authentication and policy enforcement operating at the transport layer can control network scanning and mapping and the “isolation” of network assets while providing identity to SIEMs and analytics for enhanced monitoring, audit, assessment, behavioral and adaptive response.
Building a foundation of trust in new and legacy networks starts with authenticated identity and an identity fabric that can be extended from the edge to the cloud within the network layer. This is the bedrock for the foundation of IT and OT security, providing segmentation and segregation, dynamic policy enforcement, and enhanced visualization of flows for analytics, audit, and assessments. Due to our nations aging infrastructure, segmentation of trust pedigree and providence levels will become imperative for our secure, resilient and sustained growth.
More about: Cloud Based Alternative to SCADA
FAQs about ICS Network Segmentation
What is network segmentation in information security?
Network segmentation in information security involves dividing a computer network into smaller, isolated segments. This helps control the flow of data and restricts access between segments. By separating parts of the network, organizations can enhance security, limit the impact of potential breaches, and reduce the risk of lateral movement by attackers.
What is the purpose of ICS network segmentation?
The purpose of Industrial Control System (ICS) network segmentation is to improve the security and operational resilience of critical infrastructure. By isolating different parts of an ICS network, such as process control, safety systems, and enterprise IT, organizations can prevent unauthorized access, contain potential incidents, and ensure that disruptions in one segment don’t affect the entire infrastructure.
What are the different types of ICS network segmentation?
There are several types of ICS network segmentation, including physical segmentation, where network devices physically separate segments; VLAN-based segmentation, which uses virtual LANs to isolate segments; and firewall-based segmentation, where firewalls control traffic between segments. Zones and conduits segmentation involves grouping systems based on functionality and controlling communication between them.
Why Should We Segment ICS Environments?
Segmenting ICS environments is crucial to protect critical processes from cyber threats. It limits the potential attack surface, reduces the spread of malware, and helps prevent unauthorized access to sensitive systems. Effective segmentation also aids in compliance with industry regulations and standards, enhances incident response capabilities, and minimizes the impact of security incidents on industrial operations.
Originally this article was published here.
 This article was written by Michael Murray, the Sr. Vice President & General Manager of Cyber Physical Systems (IoT) at BlackRidge Technology. He is an experienced strategic technology product and market development leader in IoT enabled devices, Autonomous and Intelligent sensors, Cyber Physical Security Solutions and Cloud / Algorithm based business development.
This article was written by Michael Murray, the Sr. Vice President & General Manager of Cyber Physical Systems (IoT) at BlackRidge Technology. He is an experienced strategic technology product and market development leader in IoT enabled devices, Autonomous and Intelligent sensors, Cyber Physical Security Solutions and Cloud / Algorithm based business development.



