[Cybersecurity] Ensuring Business Continuity with Blockchain Distributed Storage
One of DARPA’s original design features of the Internet was to ensure connectivity is resilient to partial failures. This was achieved through decentralization and recovery from failures. With more and more data stored online, we need a similarly robust infrastructure. Any ICT department would be interested in preserving their data during and after network compromise. All networks are susceptible to compromise, arriving in a variety of different ways, such as natural disaster, terrorist activity, malicious intent, or technical and equipment failures, to name some.
Blockchain is useful beyond its original purpose as a decentralized, immutable bitcoin transaction ledger. We recently looked at numerous use cases, including blockchain for supply chain provenance tracking and risk analysis (related to our SCRAMS technology).
We outlined a blockchain solution for a government agency for preserving mission-critical data under the most extreme network compromising attacks. During this effort, it became clear that such network resilience would be beneficial and applicable to nearly any networking environment and everyday data storage infrastructure.
You can see our proposed solution approach in the high-level diagramming abstraction below. The blue nodes are, of course, the network participants, be they devices, systems, etc. The orange qualifiers describe some of the supporting technology of the resilient blockchain storage solution. And the input actors on the left represent actions on the network. Network compromising actions are included for simulation and solution demonstration purposes.
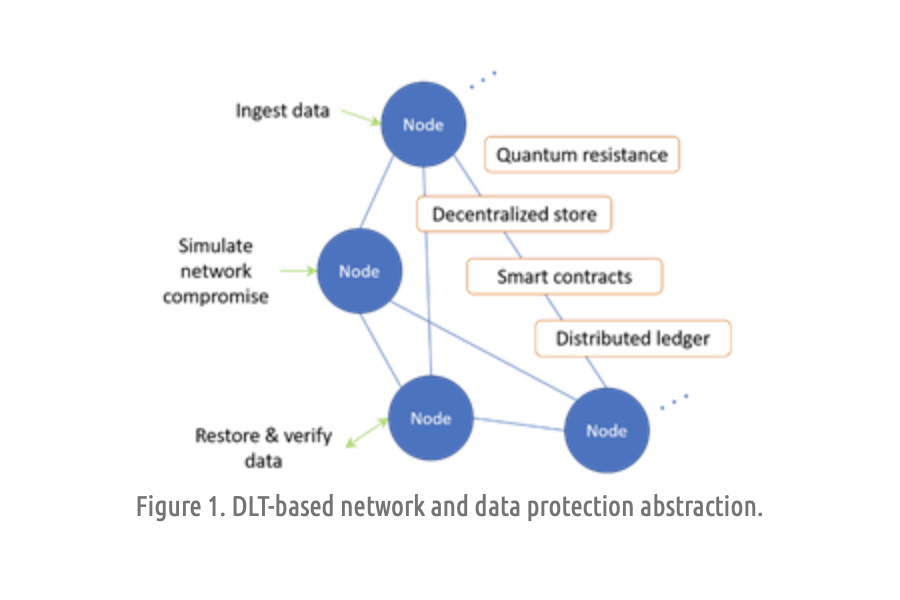
Having the solution be a drop in for existing network storage solutions would be ideal. Therefore, we consider the incoming actions as standard database queries, be they SQL or NoSQL. Conceptually the query language doesn’t matter.
We then create smart contracts that bridge the queries with the unique backing store of the resilient blockchain. We introduce the idea of Smart QUERY Contracts.
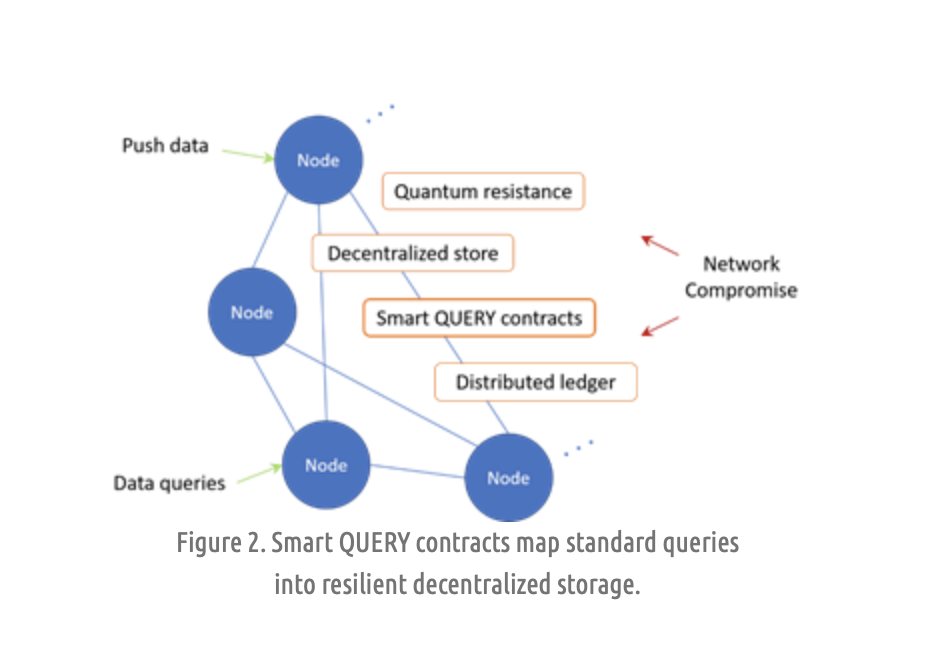
The data pushes and queries would function regardless of compromising attacks or situations, short of complete network devastation. The smart query contracts do all the work of translating, distributing the data, and putting it back together as needed to honor queries, all using standard DB query languages.
Writing the data pushes and queries into the ledger would further provide an automatic audit trail.
Based on our preliminary research, such an architecture should be able to recover from failures affecting a significant portion of the decentralized network, may be caused by human error, storage technology failure, electromagnetic pulses (or nuclear radiation) damaging microelectronics, etc.
This article was written by Edward Hackbarth and Ulrich Lang from ObjectSecurity. The original version of the article can be accessed here.
Sorry, the comment form is closed at this time.




Pingback: [Cybersecurity] Ensuring Business Continuity with Blockchain Distributed Storage