Golidlocks problem of mobile device security in organizations
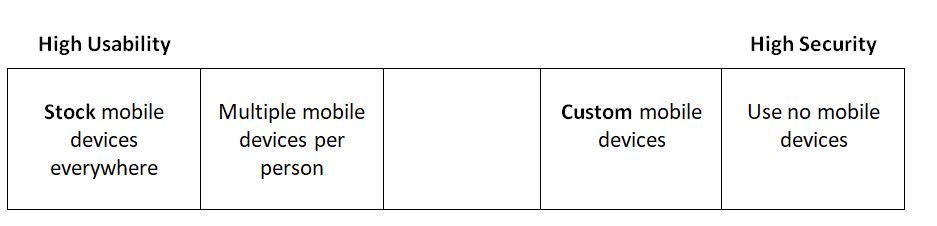
Usability vs. Security
The “Goldilocks and the three bears” story begins with a girl tasting porridge. The first bowl is too hot, the second is too cold, and the third is “just right.” This article considers mobile device security for organizations.
The theme is trade-offs between usability of the device and security for confidential organizational data such as conversations, messages, documents, images, and locations. The confidentiality and integrity of the data are key. However, if the usability of devices for end-users, administrators, and the organizations is too challenging then the availability of the data for productive work is lost.
Stock mobile devices are easy-to-use and maintain. They are the product of billions of dollars of on-going investments in hardware and software. The challenge with stock devices is they can inadvertently leak data given the large numbers of supply chain partners in app development.Plus, the many consumer-oriented business models where privacy is exchanged for services.
Custom mobile devices do a better job in securing data at rest and in transit (DAR/DIT) but can bring with them different challenges in the user experience (UX) and difficulties in maintenance, especially given the pace of updating and patching for Common Vulnerabilities and Exposures (CVE).
Adversaries are motivated to find new kinds of attacks, primarily where they are sponsored by nation states, organized crime, or terrorist organizations. The usability-security spectrum spans from stock devices maximum usability everywhere to no mobile devices anywhere to support maximum security.
COTS mobile devices and MDM management
Some organizations have relatively modest security needs and deploy fleets of stock mobile devices –Consumer Off the Shelf (COTS) devices. They are easy-to-use and affordable, although the apps, settings, and accessories used with them may inadvertently leak data.
Fleets are managed via Mobile Device Management (MDM) software and monitored by Mobile Threat Detection (MTD) / endpoint protection software. They are used in conjunction with Virtual Private Network (VPN) for network security and Multi-Factor Authentication (MFA) software for Identity and Access Management (IAM). These software stacks work well with high-end devices from reputable manufacturers. However, off-brand and lower-tier devices can leave organizations vulnerable where:
- Security patches are not made available from the manufacturer or carrier;
- The timing of patch releases is too slow; or
- Malware has been introduced or known by way of unpatched vulnerabilities left in place from the factory.
Adversaries look to have the lowest-level device access possible, ideally to the firmware level since that allows them to compromise everything above from MDM to IAM, to specific apps.
Multiple mobile devices
An individual in the organization might have multiple security usage profiles – personal, work, and mission–specific, each with their own rules of which apps, settings, and data are available for the handling of external access, monitoring, filtering, and archiving. Most often each of these profiles is expressed as a separate device, which provides a poor user experience in itself and can flag users for special attention.
GOTS mobile devices
Several custom mobile devices have been built with customized hardware, firmware, or software which solve the issue of security. The most well-known of these include Boeing’s Black Phone and General Dynamic’s Sectera Edge (SME PED) made for the U.S. government – so called Government off the Shelf (GOTS) devices.
The challenge of these devices included weak user experience, to the point that end-users did not want to use the device. Also, the device flagged the user as a government agent. Organizationally, the difficulty and cost of maintenance for end-to-end custom environments were r factors, beginning with potential expenses ranging from $3,000 to $5,000 per device and requirements for specialized back-end infrastructures.
No mobile devices
Secure areas within organizations typically have no mobile usage policies, where devices have to be left in vehicles or lockers outside the area, or stowed in TEMPEST-shielded bags or enclosures. The challenge is that so much of organizational workflow is now mobile-based and in seeking to prevent data leakage from mobile microphones, cameras, wireless connections, and other means the baby is thrown out with the bathwater. Typically the presence of active devices is monitored or blocked as a precaution to prevent subterfuge, but tethered usage should still be possible.
Multiple secure spaces
CIS Mobile analyzed the problem space, looking for a way to retain the hardware, software, maintenance, and banality advantages of COTS devices along with the security features of GOTS devices, without re-inventing the challenges of usability, attention-grabbing customization, maintenance, and high costs.
Two use cases stand out as defining the secure usability dilemma:
- Multiple Independent Levels of Security (MILS) for personal, work and various mission spaces that can run in parallel and be switched easily in real-time.
- In secure areas turn off the microphones, cameras, speakers, and wireless communications at the Operating System (OS) level;cutting access forall other enterprise tools and apps built above.
CIS implemented these features in an alternative version of the Android OS – altOS -based on the Android Open Source Project (AOSP). The goal was to deliver a “Goldilocks” solution that retained compatibility with stock devices, carriers, enterprise MDM, MTD, VPN, and MFA tools as well as app ecosystems.
 This article was written by Simon Hartley. He works with government customers at CIS Mobile with its altOS mobile security platform. He also worked with Apple and Samsung in hardening their mobile devices for U.S. government use and is a frequent speaker on cybersecurity at industry events.
This article was written by Simon Hartley. He works with government customers at CIS Mobile with its altOS mobile security platform. He also worked with Apple and Samsung in hardening their mobile devices for U.S. government use and is a frequent speaker on cybersecurity at industry events.



