[Use Case] Smart Grid and Distribution System Cybersecurity Protection
Smart grid is an evolving new power system framework with Information and Communication Technology (ICT) driven power equipment and a massively layered structure. The new generation sensors, smart meters and electronic devices are integral components of smart grid. However, the upcoming deployment of smart devices at different layers followed by their integration with communication networks may introduce cyber threats and this is why smart grid security is very important.
Smart Grid Security Overview
Ten years ago, the energy grid was still a fully stand-alone system. Now, it gets more connected by the day. Non-secure systems are added, and existing non-secure systems get more exposure into an increasingly complex architecture of the overall grid system. Criminal actors have identified opportunities to create business models with malware such as ransomware; nation state actors explore capabilities in hybrid warfare. If the energy grid is hacked, you may lose lives
The interdependencies of various subsystems functioning in the smart grid, if affected by cyber-attack, may be vulnerable and greatly reduce efficiency and reliability due to any one of the devices not responding in real time frame. The cybersecurity vulnerabilities become even more evident due to the existing superannuated cyber infrastructure.
Smart Grid Explained
The Smart Grid can be simplified and represented in four different layers:
- Physical Layer: including Generation (cycling coal and natural gas-fired power plants with CCS, grid-based renewables, wind farms, nuclear power plants), Transmission, Distribution, Consumption and Grid-based Storage. The electrical flows are limited to this layer.
- Communication Layer: including home area, neighborhood, access & black-hole, core, office and external networks.
- System Integration Platform: computing infrastructure, networks and security management, application and data integration.
- Software layer: meter data analysis (MDA), billing, outage management, load control, consumers and field engineers’ devices interface, GIS, wide area management systems, consumer information systems.
The security requirements for the Smart Grid are covered by the CIA Triad (Confidentiality, Integrity and Availability). The CIA triad applies to both the General-Purpose Information Technology Systems (ICT Component) and the Industrial Automation & Control Systems (ICS Component).
Smart Grid Security and Managing Risks
Nevertheless, when it comes to managing the risks, prioritization and strategy, it is important to differentiate between the ICT component and the Industrial Control Systems (ICS) component.

- Availability: focuses on identifying and assuring data and services that need to be available. This is a critical aspect for Smart Grids systems supporting the Smart Grid automation, for example for SCADA servers of Distributed System Operators (DSO) or Transmission System Operators (TSO).
- Integrity, ensuring the fidelity of the information, which means identifying and preventing data to be modified without authorization. An example might be to guarantee that control commands and power control readings have not been modified during their transmission.
- Confidentiality, preventing unauthorized access to private information. This is less critical when considering grid automation systems (SCADA) but absolutely crucial for end consumers.
- There are two other security dimensions that need to be considered: authentication and non-repudiation.
- Authentication has been considered implicitly in the CIA Triad and deals with making sure that someone or something really is who or what it claims to be.
- Non-repudiation refers to being able to prove that an action has been taken by the entity really responsible for that action. These two components are equally important for Industrial Automation & Control Systems (SCADA) and General-Purpose Information Technology Systems.
Smart Grid Architecture
Considering that ICT layers constitute roughly three quarters of the Smart Grid architecture, the major challenges below will be easily understood:
- Connectivity: as the topology of the Smart Grid is decentralized, all the elements require a high level of protection. The communication network, while allowing for significant advantages, also brings with it risks and challenges. It is key to striking a balance between internetworking and data security.
- Trust: consumers are no longer assumed to be trustworthy
- Privacy: the introduction of smart meters brings important challenges in terms of consumers’ information privacy.
- Software vulnerabilities: it is especially important to protect SCADA systems from malware, malicious updates as well as having a strict patching policy.
Cybersecurity in the Smart Grid must address not only deliberate attacks, but also inadvertent compromises of the information infrastructure due to user errors, equipment failures and natural disasters. Vulnerabilities might allow an attacker to penetrate a network, gain access to control software and alter load conditions to destabilize the grid in unpredictable ways.
Lack of Smart Grid Security Risks
The risks of the IIoT is far greater when looking at critical infrastructure and Industrial Control Systems (ICS) of manufacturers, power grids, water systems, city infrastructures and nuclear plants. This growing number of endpoints connected to the Internet increases the cyber-attack surface – each class of endpoints and their cloud service provider infrastructure introduce new vulnerabilities and attack vectors. No one wants to see that critical systems fail, and necessary precautions need to be implemented to eliminate any level of risk where possible.
Programmable Logic Controllers (PLCs), industrial gateways and switches and other IIoT devices should not be clone-able and should contain unique Identities. Using IP or MAC addresses for identity with existing network security infrastructure is not sufficient for securing the IIoT. Assured identity is needed for devices connected to the network, for determining what ingress or egress traffic can be initiated to or from these network endpoints. This eliminates the need to use network addresses and location for security policy. More about The Importance of Security by Design for IoT Devices
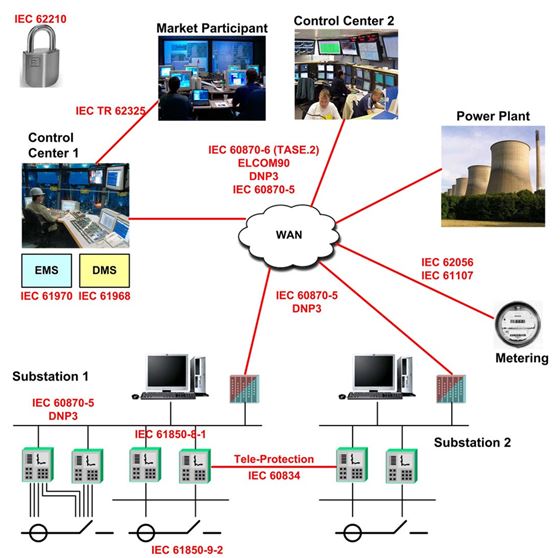
Deterministic and controlled network connectivity is critical to protecting IIoT devices and systems. A zero-trust approach using identity can be used to prevent unauthorized traffic, the security methods should be fluid enough to allow rapid change in policies as necessary. More about The Role of IoT in Smart Grid Technology and Applications
BlackRidge addresses these core network security requirements, leveraging identity for software-based micro-segmentation. With our solutions in place, ingress, egress and network access is fully controlled and the attack surface is greatly reduced. Network devices are cloaked and there is no ability for zero day or DDoS attacks because the IIoT devices are simply not reachable.
Our micro-segmentation with adjustable trust levels can create an overlay virtual network based on identity that works with heterogeneous environments. This enables different policy access controls, analytics and traffic engineering on a per identity basis across multiple spans of control and different vendor equipment. The control plane of the networks themselves is also a key area that will be isolated and protected. Why using network virtualization?
Consider the diagram above and the various components in a DSO; notice the protocols between the various elements. A majority of these run on top of TCP/IP which by default can be protected or cloaked by us.
More about Cybersecurity Vulnerabilities in ICS Mobile Applications
BlackRidge Key Benefits
- Blocks Unidentified Traffic
- Blocks Unauthorized Traffic
- Blocks Unauthorized Network Scanning and Discovery
- Blocks Zero-day Attacks from Unauthorized Devices
- Blocks Unauthorized Encrypted Traffic
- Blocks Unauthorized Adversary Traffic with Spoofed Addresses
- Blocks Unauthorized Adversary Traffic with Spoofed Content
- Enables Responsive Analytics Integration
- Enables Cyber Defense Automation
Solution Summary
- Use identity-based networking
- Policies automatically adapt regardless of infrastructure changes
- Control ICS and SCADA deployments through micro segmentation and network cloaking to prevent zero day and DDoS attacks
- Instant connect and revoke remote access to specific systems regardless of the topology
- Isolate critical resources
- Track and record all access via identity
- Eliminate the need to change access control list, routing rules and firewall policies.
![]() Mike Miracle is a senior marketing and operations executive with extensive experience in networking, security, virtualization, and storage software. He has built and led global marketing operations, most recently at SevOne, and he has consulted for and advised over 25 technology companies on strategy, operations, and M&A. Mr. Miralce led corporate development for VERITAS Software during it high growth years, and he has held senior technology management and software development positions at HP, Novell, and Bell Labs.
Mike Miracle is a senior marketing and operations executive with extensive experience in networking, security, virtualization, and storage software. He has built and led global marketing operations, most recently at SevOne, and he has consulted for and advised over 25 technology companies on strategy, operations, and M&A. Mr. Miralce led corporate development for VERITAS Software during it high growth years, and he has held senior technology management and software development positions at HP, Novell, and Bell Labs.



