How phishing is affecting manufacturing and other industries
For hackers, phishing is easy. And profitable. The average phishing attack costs a mid-sized company $1.6 million.[i] No wonder the number of phishing attacks shot up 65% worldwide last year.[ii] For many years, organizations have invested in technology to keep them safe from malicious emails. Yet ransomware, CEO fraud/business email compromise (BEC) and breaches stemming from phishing emails inflict a heavy toll. According to the FBI, BEC alone cost businesses worldwide over $5 billion from 2013 to 2016.[iii] Here’s the disconnect: phishing skirts technology by targeting human beings. That’s why it’s critical to educate employees to recognize and report all manner of phishing attacks.
PhishMe released its third annual Phishing Resiliency Report , which examines controlled phishing activity and phishing susceptibility at global organizations across 23 industries, including the manufacturing/energy industry. Across the board, resiliency is improving throughout major industries; in fact, 7 out of 8 industries have seen resiliency harden.
Breaking down susceptibility
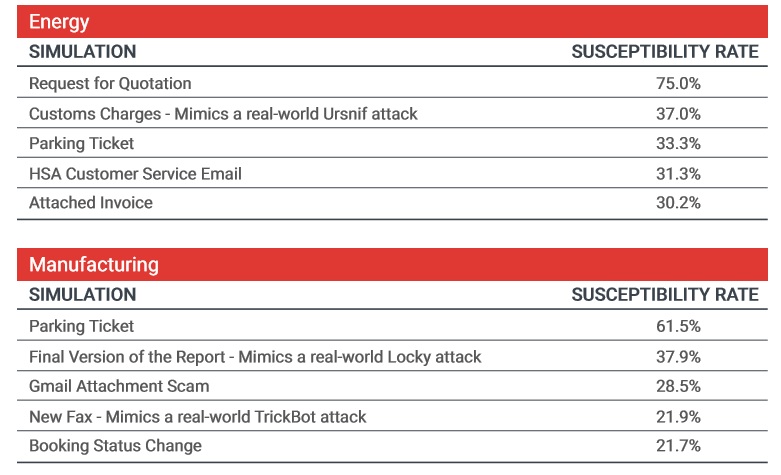
What’s happening in your industry is important to your organization. This PhishMe Simulator data on threats in different verticals can help you decide which phishing tactics to add to simulations. Each of these threats is active and considered high-risk.
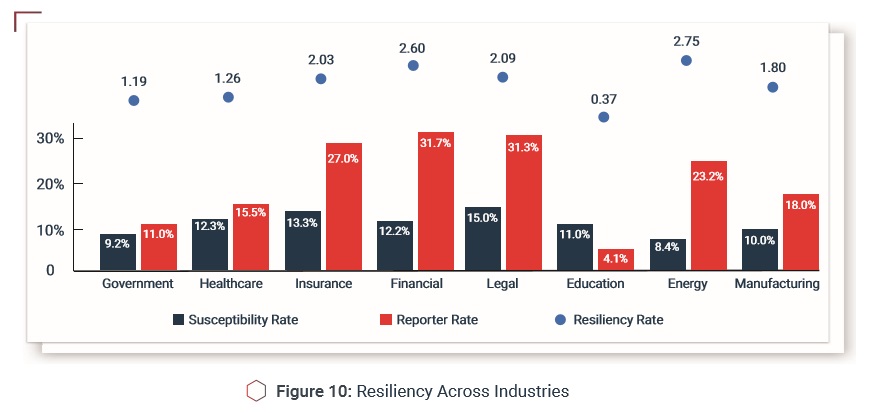
In 7 out of 8 industries, resiliency has hardened
As with susceptibility and reporting, resiliency is improving throughout major industries. Education is the exception. Possible reasons: tighter security budgets compared to other industries, lack of central control and typically open environments that encourage users to “bring your own device.”
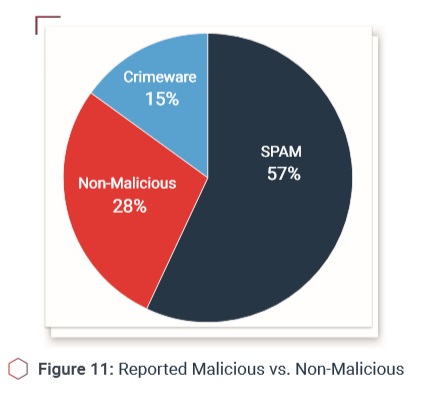
Users are reporting real threats
Most of the data in this report is from phishing simulations. But what about real attacks—how do conditioned employees react? They report real threats, that’s how. Over the first eight months of 2017, our Managed Triage users identified over 216k emails, 15% of which were malicious, containing malware and bad links.
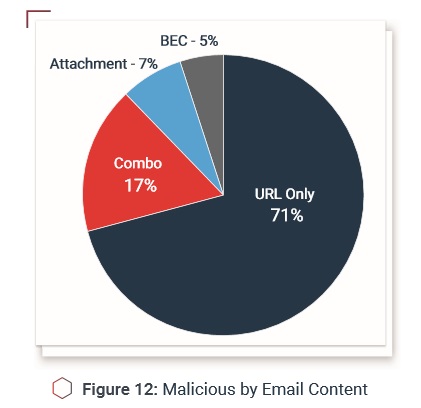
Identified malware inclu des DELoader, Pony and Loki and other widespread threats. The top threats from compromised internal sources were “fakery” such as account checks or IT Help Desk messages; the top external threat was bogus order payment. Drawing from phishing intelligence, simulations of new attacks can be quickly crafted and run. The attack methods incident responders see, along with fresh phishing intelligence, should be regularly woven into simulations. This keeps anti-phishing programs relevant and potent.
Below is an example based on a real phish that uses Office Macros to distribute the Smoke Loader Downloader and Monero Minor Bot (and previously the Zyklon HTTP Trojan).

Here is the list of threats identified by PhishMe Intelligence over the course of one year.

It’s well known that phishing, like all forms of cyber-crime, constantly evolves as attackers seek an edge. The data in this report points to another evolution: that of organizations refining anti-phishing programs to blunt the attacker’s advantage.
Recommendations
The “kill chain” is a well-known model among security professionals. The idea is to outline, link by link, the chain leading to a security incident and take all steps to prevent it. In the phishing kill chain, you want to stay “left of breach” (see illustration below). In short, here’s how to utilize this model:
- Be transparent and educate users on standard phishing clues and the purpose of the program.
- Baseline your organization’s technical and business process weaknesses, so you can target them during initial simulations.
- Run diverse simulations and analyze each for high susceptibility to active threats.
- Design follow-up simulations based on known deficiencies and analysis of first results.
- Stress the importance of reporting in all simulations and awareness activities.
The data reflects the experiences of some 1,400 PhishMe customers across the globe, including Fortune 500 and public-sector organizations across 23 industries. In some instances, the data goes back to 2014 or 2015 to show longer-term trends or may focus on a specific time frame. In other cases, the data is from the past eight months, January through August 2017. The foundation of this data is 52.4 million simulation emails. As in the past, the emails were written in numerous languages, 15 to date.

[i] Cloudmark, “Spear Phishing: The Secret Weapon Behind the Worst Cyber Attacks,” 2016.
[ii] The Anti-Phishing Work Group, “Phishing Activity Trends Report,” 2016.
[iii] Cloudmark, “Spear Phishing: The Secret Weapon Behind the Worst Cyber Attacks,” 2016.
Access the full report here.
Sorry, the comment form is closed at this time.




Pingback: Phishing Attacks in the Manufacturing Industry