Impact to large-scale implementations: Smart factories and smart cities
In this article we discuss how insecure deployments and the lack of well-defined security in M2M technology can be abused to turn into unforeseen problems in critical and large-scale environments like smart factories and cities.
M2M technology forms the core of IIoT systems for maintaining smart factories and building smart cities. As more of these connected environments crop up, the more it becomes difficult to manage and protect large volumes of data exchanged by the IoT-enabled devices.
While looking for leaked data related to smart cities, the research team noticed a group of records that contained email addresses and location names of certain businesses. All these records were taxi or car-sharing rides booked by employees traveling to and from their offices. The records furthermore contained precise timing information that could allow an attacker to learn who was going where.

Taxi or car-sharing data containing business names and business email addresses
The team also found instances of data exposure related to the manufacturing sector. Records were leaked by a programmable logic controller (PLC), which was sending out telemetry data via an open MQTT broker. Exposed records could indicate names assigned to particular control systems, details of the manufacturing processes, and even urgent maintenance requests like the one below.
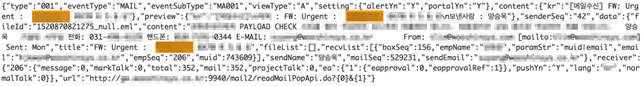
Urgent alert or maintenance request for a company specializing in the manufacturing of the automotive body assembly system and body parts
Such information can be used for target reconnaissance so that connected machines or employees of potentially high-profile companies can be tracked. These are just two examples of how exposed data in smart cities, factories, and even certain sectors could allow an attacker to prepare for an attack with the help of leaked sensitive data.
Note on misclassified records: We acknowledge the presence of a minority of misclassified records, due to the non-exhaustive keyword list that we used, and due to generic content (e.g., news) circulating over MQTT or CoAP, which could likely match any of the keywords. To minimize the ratio of false matches, we manually vetted each of our searches and removed outliers.
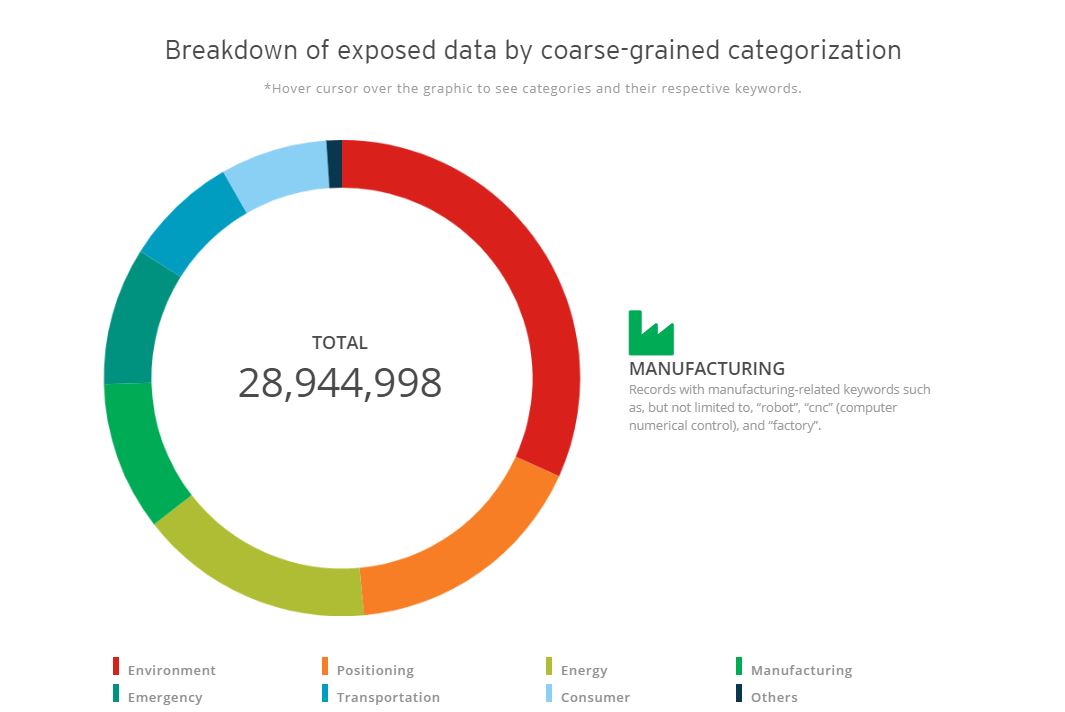
For the other industries stats, please click here.
Securing IoT protocols for reliable M2M communications
The number of connected devices and machines has nowhere to go but up, and more and more critical services are relying on communication protocols to provide immediate and essential response. This gives further responsibility to manufacturers and service providers to ensure both the reliability and the security of protocols and applications.
Considering the emergence of these protocols, it’s reasonable to expect that attackers will catch up and abuse M2M technology for their malicious activities. We even expect poisoning of telemetry data to be a feasible and indirect attack method in the future.
Certain considerations like not having security built in and protocols having concepts such as wild-card topics and linked resources can be turned against users by exposing their resources and collecting data about them. Moreover, MQTT and CoAP do not check the data or payload that they transport, which means that the information can be really anything, posing data validation issues on the connected systems.
Organizations and manufacturers should then pay adequate attention to IoT and IIoT security. Organizations’ security teams should ensure that proper security mechanisms are in place when using protocols. Solutions do exist to secure M2M communications — they are just not employed by all.
It is very important for organizations to conduct risk assessments. This research aims to raise awareness on potential risks in IoT and IIoT devices that use MQTT or CoAP, help organizations to identify weak points in their deployments, and follow the best practices we outlined in the paper. For in-depth analyses and insights, read “The Fragility of Industrial IoT’s Data Backbone: Security and Privacy Issues in MQTT and CoAP Protocols.” In this research, it’s discussed how attackers can subvert MQTT- and CoAP-enabled implementations and even take advantage of exposed data that includes personal and company-sensitive information for attacks. Find out how MQTT Enables IIoT Security Best Practices within the Purdue Model.
This article was written by Trend Micro Research with EURECOM and Politecnico Di Milano (POLIMI) and originally was published here.



