Released this week: Global ICS & IIoT Risk Report
Industrial and critical infrastructure organizations that rely on industrial control systems (ICS) to run their businesses — such as firms in energy and utilities, oil & gas, pharmaceutical and chemical production, food & beverage, and other manufacturing sectors — have known their valuable assets are susceptible to cyberattack since Stuxnet was discovered and publicized in 2010.
The extent to which they are vulnerable, and the attack vectors through which they might be compromised, however, have historically been much harder to know in any measurable sense.
More recently, destructive malware such as WannaCry and NotPetya, as well as targeted ICS attacks such as TRITON and Industroyer, have shown the potential impact of ICS cyberattacks which include costly production outages and clean-up costs, catastrophic safety and environmental incidents, and threats to the proper functioning of civilized societies such as loss of heat, power, and even human life.
In 2017, CyberX began to shed light on these risks when we published the first-ever Global ICS & IIoT Risk Report. By analyzing real-world network traffic data from 375 production ICS networks worldwide, across multiple industry verticals, CyberX gave the world a data-driven glimpse into the wide range of existing vulnerabilities in ICS environments.
This report supplements the data included in our 2017 report. It analyzes data obtained from over 850 production ICS networks that CyberX assessed from September 2017 to September 2018, using proprietary Network Traffic Analysis (NTA) and deep packet inspection1. The networks span all sectors across North and South America, EMEA, and Asia-Pacific.
This follow-up to our previous report remains one of the only ICS risk analyses based on actual network traffic data — as opposed to interviews or survey-based data — in existence.
The data clearly shows that industrial control systems continue to be soft targets for adversaries. Many sites are exposed to the public internet and trivial to traverse using simple vulnerabilities like plain-text passwords. Lack of even basic protections like automatically-updated anti-virus enables attackers to quietly perform reconnaissance before sabotaging physical processes such as assembly lines, mixing tanks, and blast furnaces.
As Sun-Tzu advises, those who know neither their adversaries nor themselves are doomed to lose battles. In order to protect ourselves, our critical systems, and our economies, we need a realistic, data-driven view of the current risk.
This is an excerpt from the 2019 CyberX Global ICS-IIoT Risk Report. Download it here.
A few highlights from the report

Source: Highlights from 2019 CyberX Global ICS-IIoT Risk Report
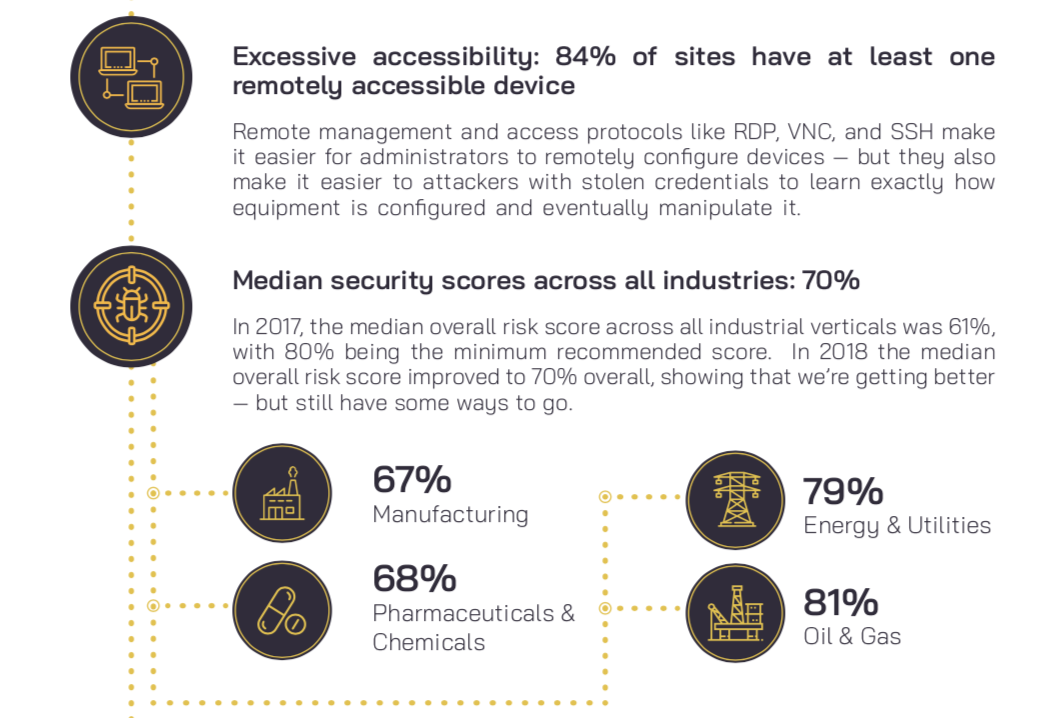
Source: Highlights from 2019 CyberX Global ICS-IIoT Risk Report