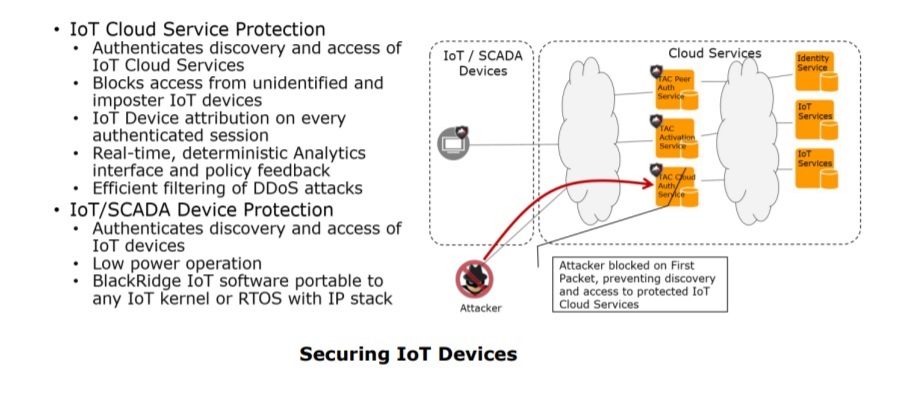
Securing IoT Devices and Traffic between IoT Sensors and Cloud Analytics
It is well documented that IoT devices have introduced new security risks. Most IoT devices must interface to cloud based management and analytics engines and therefore support a TCP/IP stack for this communication. Our IoT endpoint software is designed to augment a device’s TCP/IP stack with very little overhead, providing authentication to the cloud services.
Informational components are all about the sensors. Sensors have a calibration that provides information within specific tolerances providing known levels of data fidelity. IoT sensors may produce different information at different tolerance levels, but the receiving analytic system must know what tolerance to apply to each reported measurement. This enables the sensors to provide the necessary input for bounded operation.
From a network perspective, sensors need to operate independent of the underlying network topology, reporting the network traffic from their deployment viewpoint. At the same time, physical sensors must be physically secured and tamper evident to prevent their removal or relocation. When sensors are deployed on endpoints, they must be cryptographically secured to their host, again to prevent removal or relocation. In order for sensors to provide trusted measurements, each sensor must have a unique identity that can be easily authenticated. Identity authentication enables analytics systems to discern both missing and inauthentic sensors.
Sensors may have some level of internal processing capability. Intelligent sensors may even have local analytical capabilities to enable them to detect complex signals and filter them before communicating them to a higher level analytical system. A challenge with deploying intelligent sensors is that they must be designed and implemented to ensure that the sensor itself is not providing a new attack surface that is vulnerable to compromise. All sensor data, including data internal to the sensor must be protected from attacks.
Further reading: Tips for Powering the Trillion Sensor Industrial Internet of Things Dream
The Importance of Security by Design for IoT Devices
Sensor authentication and sensor data must be easily authenticated and sensor data should be efficiently collected and securely communicated to the analytics system within an expected period of time. To address scalability of large number of sensors, intermediate sensor aggregation points may aggregate and preprocess data on the way to the analytics systems. This is done primarily to limit the volume of sensor data that must be ingested directly by the analytics systems. Most sensors have an upper bound limit for reporting determined by the interface bandwidth supported by the sensor itself. We provide a scalable solution for IoT sensors that has very little overhead to the existing architecture.
This is an excerpt from the “A Next Generation Security Architecture for IoT and Blockchain Infrastructure” whitepaper.
John Hayes is a co-founder of BlackRidge Technology and has served as its Chief Technology Officer since its inception. Mr. Hayes is a technology entrepreneur who specializes in cyber security, networking, I/O interface design, storage architecture, and communications protocols. He has a proven track record of bringing concepts to market and is able to clearly communicate complex ideas to diverse audiences.

