Study Shows 80% of Companies Admit to an Email Security Breach Last Year
Even with the increased use of Microsoft Teams, Slack, and many other multi-functional messaging services, email remains a critical communication tool for most organizations. OPSWAT partnered with Osterman Research to conduct a study to analyze email security breaches in critical infrastructure sectors, identify the most common types of attacks, and analyze success metrics for email security. The study showed most organizations had experienced one or more email-related security breaches over the past year and fully expect these breaches to increase over the coming year as well. Unfortunately, people working in these sectors pose extremely attractive targets for cyber threat actors, putting them under constant threat of attack. Organizations can use this research to understand email-related threats better and evaluate how best to address these challenges in the year ahead.
The Email Security Breach Landscape
The research showed that organizations experienced multiple types of attacks, including successful phishing incidents, email login credential compromises, data leakage, ransomware infection, and malware infection. Up to 65% of the organizations in the critical infrastructure sector reported that they had been the victim of an email security breach in the previous twelve months, with another nearly 15% declining to share whether they had been the victim of an email-related breach (a reluctance that likely indicates a breach did occur). Organizations surveyed also shared that the majority (an average of 63%) of all cyber security threats arrived via email.
Despite identifying email as the primary attack vector for these organizations, more than half of these organizations still operate on the assumption that email messages and related file attachments are not malicious or are somehow bothbenign and malicious by default, an assumption that must increase internal confusion about how best to handle emails and attachments. However, the approach that best aligns with the current email threat landscape is assuming that all email messages and attachments are malicious by default. Organizations that took the malicious-by-default approach were correlated more frequently with high confidence in the organization’s current email security protections.
A Simple Avenue to Disruption
Employees frequently open emails, click on links, and download or open email attachments, particularly if the message appears to come from a known source or an internal contact. While cybersecurity awareness training has long been touted as a way to avoid an incident, all too often, this approach alone is far from sufficient. Instead, organizations must implement better email security technologies than they currently rely on to prevent such threats from being delivered to inboxes in the first place.
Email-related security breaches in the previous 12 months: number of breaches per 1,000 employees

The reality is that cyber threats and nation-state actors are continuously identifying new ways to compromise targets in the critical infrastructure sector. This focus is partly because of the massive disruptions successful attacks pose to physical infrastructure and the network of devices and controllers that allow this infrastructure to operate. For malicious actors, attacks provide a more guaranteed avenue for successful extortion, while nation-state actors know that disrupting normal operations is both unsettling and even potentially deadly for the targeted country.
Confidence Low as Successful Attacks Rise
Nearly half (48%) of critical infrastructure organizations in this research indicated that they were not confident that current email security protections were sufficient to repel email-borne attacks. Also concerning, just 34.4% were able to state that they were fully compliant with relevant email-related regulations, such as GDPR and other privacy regulations. In addition to not aligning with regulatory requirements, too few organizations have adopted advanced email security capabilities that prevent email security threats from reaching their users’ inboxes.
Email security capabilities lacking at critical infrastructure organizations
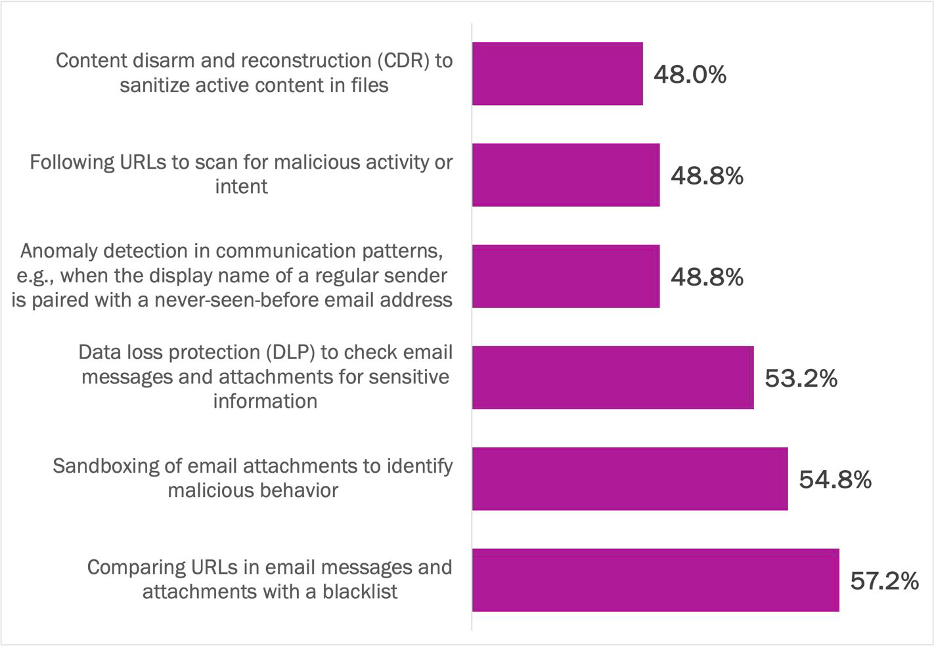
Some effective email security capabilities for critical infrastructure include content disarm and reconstruction (CDR), which sanitizes active content in files, such as macros or code; assessment of URLs for malicious signals every time a URL is clicked or opened; detecting anomalies in communication patterns to identify impersonation attempts; and data loss protection (DLP) solutions to check for sensitive information in email messages and attachments. These capabilities align with the malicious-by-default principle of email security, which enables a zero-trust approach that is appropriate for the escalating threats directed at critical infrastructure organizations.
An Aspiration to Improve Email Security
While results from this survey are certainly mixed and quite alarming in some areas, the good news is that the organizations that participated in this research plan to significantly improve their email security posture in the coming year. While currently only 54% are confident in current email security protections, nearly 75% intend to reach this level in the next twelve months. Many more wish to achieve the highest level of confidence in this area, increasing from just 6.8% that are currently extremely confident to 34.8%. This goal is achievable for organizations that leverage zero-trust technologies for email security, bring additional professional skills in-house, and invest sufficient budget in email security solutions to preclude incidents from occurring. Such efforts will reduce risk and increase peace of mind for citizens worldwide who rely on the stability and availability of critical infrastructure.
Read the full report by Osterman Research
About the author

This article was written by Itay Glick. He serves as Vice President of Products at OPSWAT and brings more than 17 years of executive management experience in cybersecurity at global technology companies based in the U.S., Europe, and Asia.


