The Digital Cybersecurity Paradox
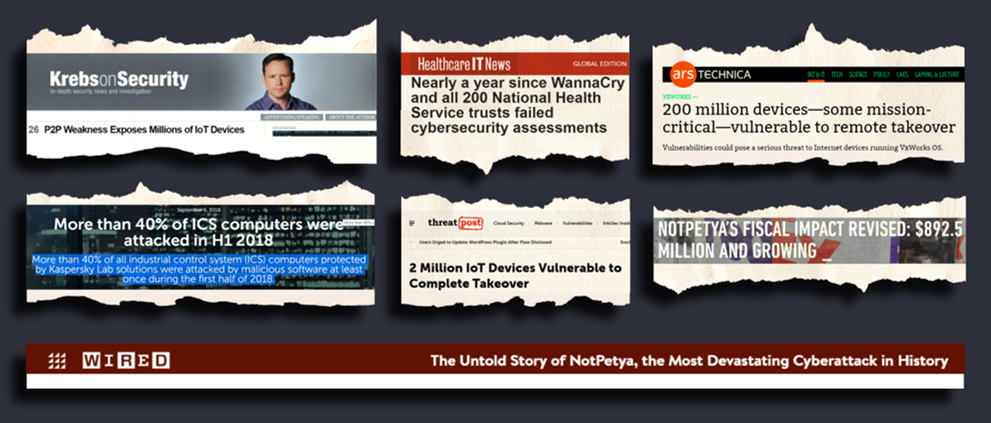
In 5 years there will be 75 billion devices connected to the internet, perhaps a few billion insecure and unpatchable. An estimated 2 billion run VxWorks and perhaps a couple hundred million of those will not be patched in any reasonable length of time.
About 200 million Internet-connected devices—some that may be controlling elevators, medical equipment, and other mission-critical systems—are vulnerable to attacks that give attackers complete control, researchers warn. – Ars Technica
Deep Asset Risk
It’s no longer just about data exfiltration but instead also the specter of the loss of physical control. Thanks to the overwhelming business advantage of digitalization many organizations are creating massive, porous attack surfaces of insecure devices responsible for controlling physical infrastructure, from water, HVAC and power to medical, manufacturing and even maritime structures.
What Could Go Wrong?
The digital paradox is the inherent conflict between business advantage and deep asset exposure to bad actor control. And we’ve already seen the opening moves in the new hacker game. The lines between networks, nations and organizations are getting blurred by vanish airgaps that once protected these devices from unseemly remote actors.
Unintended Consequences
Let’s face it, we’re emerging from the perfect Sorites Paradox scenario, where a heap of sand (the growing business value of interconnectivity) is eroded just one grain at a time by malware or remote bad actor control. Today, as billions of insecure devices connect, there is a growing, critical mass of exposure where many more grains can exit at a time.
I discussed this in more detail with Gabe Lowy, Tempered’s Bryan Skene and SiliconANGLE’s John Furrier a few weeks ago on theCUBE. You can read more about it as well at A Clear and Present Danger.
For example, attacks against critical infrastructure in Ukraine in 2017 (WannaCry and NotPetya) inadvertently spread globally and shut down hospitals, ships at sea and even distribution centers. They were among the most devastating and unintended cyber attacks of all time. OOPs.
These attacks aimed at Ukraine accidentally cut globally like a hot knife through warm butter, from network to network, nation to nation, seeping into the critical systems of some of the most well-defended companies. Read excellent coverage of NotPetya in Wired
IT isn’t ready for IIoT
 The firewall vendors warn you to patch and segment, segment, segment. How many skilled security experts will it take to protect you? How many lines of code? How many ACLs? The answer: you’ll never have enough resources. See this 102 second explanation from former Wall Street infrastructure analyst Gabe Lowy on the futility of the firewall in the age of IIoT:
The firewall vendors warn you to patch and segment, segment, segment. How many skilled security experts will it take to protect you? How many lines of code? How many ACLs? The answer: you’ll never have enough resources. See this 102 second explanation from former Wall Street infrastructure analyst Gabe Lowy on the futility of the firewall in the age of IIoT:
“So if you’re an organization moving IIOT data from your OT systems across your network into IP analytics systems or software, that’s lateral movement. Your firewall- traditional firewall, just not going to be able to handle that and protect against it…”
From Geeks and Greeks to Rolling Stones
 That brings us to another insight from the ancient Greeks: the myth of Sisyphus. The firewall and segmentation problem is, at its core, a scale and resilience/availability challenge exacerbated by the direct link between skills shortages and human error in the security chain. Every step up the mountain, a step back. All the while the attack surface grows and the attack vectors proliferate.
That brings us to another insight from the ancient Greeks: the myth of Sisyphus. The firewall and segmentation problem is, at its core, a scale and resilience/availability challenge exacerbated by the direct link between skills shortages and human error in the security chain. Every step up the mountain, a step back. All the while the attack surface grows and the attack vectors proliferate.
What could go wrong?
A recent theCUBE panel on IIoT and cyber war concluded that the bad guys were already in your network. They are being held back by the threat of attacks against their own soft underbellies. But what about private players who are primarily playing defense and have no offensive countermeasures?
 That is, the digital enterprise merely connecting IIoT devices to the internet? Do they launch attacks against bad actors or do they just pay ransom? Today I suspect they’re simply paying up or suffering the losses. Maybe they’ll take out cyber attack insurance.
That is, the digital enterprise merely connecting IIoT devices to the internet? Do they launch attacks against bad actors or do they just pay ransom? Today I suspect they’re simply paying up or suffering the losses. Maybe they’ll take out cyber attack insurance.
The ancient Greeks took exception to rolling stones uphill. It was a notable curse.
Think you can hire and spend your way to the top with your existing security stack? Get Gabe’s paper here.
 This article was written by Gregory Ness, Interim CMO at Tempered Networks. Gregory has an extensive startup background in networking, security, virtualization and cloud computing. He was among the first to point out network and security issues with virtualized IT infrastructures and then emerging cloud operating models, which led to the formation of the Infrastructure 2.0 Working Group with Vint Cerf, Dan Lynch and a host of leaders in the networking industry.
This article was written by Gregory Ness, Interim CMO at Tempered Networks. Gregory has an extensive startup background in networking, security, virtualization and cloud computing. He was among the first to point out network and security issues with virtualized IT infrastructures and then emerging cloud operating models, which led to the formation of the Infrastructure 2.0 Working Group with Vint Cerf, Dan Lynch and a host of leaders in the networking industry.



