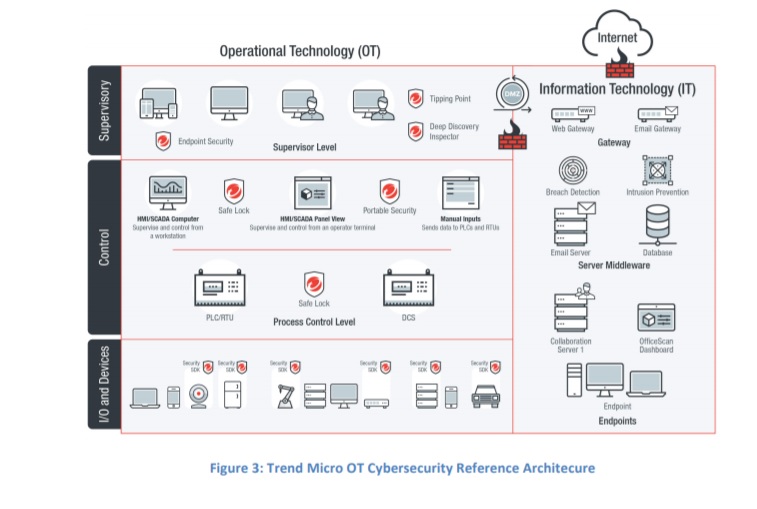
Trend Micro Cybersecurity Reference Architecture for Operational Technology
The evolution of the Internet of Things (IoT) has made life a lot more convenient and productive for both consumers and businesses alike over past few years, but on the other side, cybersecurity is an emerging challenge. For automobile original equipment manufacturers (OEMs), Tier 1 suppliers, car dealers, service providers, car owners and drivers, cyberattacks are now a reality that they have to grapple with.
In the era of the IoT, more and more key device functions rely on software rather than hardware. This is also true with vehicles. Unfortunately, as vehicles become increasingly automated and connected with the outside world, they tend to face growing security threats.
Vulnerabilities arise particularly when just-in-time manufacturing and a faster speed to market leave less time for product safety testing. These vulnerabilities might not be uncovered until millions of vehicles have been released, in which case the necessary patching procedure is all but certain to prove even more costly — not only to the affected carmaker’s finances but also to its reputation. It’s important, then, for security measures to be properly applied right from the outset of the car manufacturing process, starting in the design phase.
That is why it is important for device manufacturer to integrate security into the device itself, to ensure consumers and businesses are protected from these challenges, the minute they install your IoT device. Because of these challenges, Trend Micro have developed a cybersecurity solution called Trend Micro Internet of Thing (IoT) Security consisting of File Integrity checking, Application Whitelisting, Hosted Intrusion Prevention Services (HIPS), Network Anomaly Scanning and Detection, System Vulnerability Scanning, and Virtual Patching.
Trend Micro IoT Security (TMIS) is built-in IoT security software that monitors, detects and protects IoT devices from potential risks, including data theft and ransomware attacks. This ensures firmware integrity and reduces the attack surface, which not only prevents harm to your IoT devices, but also minimizes device maintenance costs and protects your reputation.
See other tips on how to protect your network from malware attacks.
Trend Micro’s IoT cybersecurity software
Trend Micro SafeLock for IoT
System Lockdown Software for Fixed-Function Devices
This solution protect fixed-function devices such as industrial control systems and embedded devices, terminals in a closed system, and legacy OS terminals against malware infection and unauthorized use. Trend Micro SafeLock for IoTT prevents the execution of malware with lockdown.
Lockdown is a technique that limits a system to running only day-to-day operations while controlling system resources and access. Where most anti-virus software uses blacklisting to forbid known malware from running, SafeLock uses whitelisting to allow only known and approved processes to run. The set of applications that run in fixed function devices is essentially static, making whitelisting practical and eliminating the need to regularly update a blacklist. SafeLock’s approach has a limited impact on system performance and can improve an organization’s capacity to analyze log files. Trend Micro SafeLock for IoT can protect terminals reserved for critical control systems, embedded devices, and legacy OS terminals. Also, its easy user interface and cooperation with Trend Micro Portable Security enables rapid deployment and a high degree of operability.
Trend Micro Portable Security 2
Malware Scanning and Cleanup Tool for Standalone PC & Closed Systems; No Internet connection does not mean safe and secure.
The Internet is not the only way that malware can infect PC. A Trend Micro survey of companies in Japan found that 20% of stand-alone computers and PCs in closed networks were infected with malware. Devices brought in from outside the system by users, as well as the use of USB flash drives, can infect stand-alone PCs and those in close systems.
Organizational restrictions on installing software on these PCs means that virus protection software either can’t be installed at all or can’t be updated to cover the latest generation of malware. Without access to the Internet, PCs that do have anti-virus software installed are difficult to scan with the latest malware pattern file.
The Portable Security for IoT hand-held tool plugs into a USB port to detect and eliminate malware, without the need to install software on the PC. The tool changes color to indicate whether or not it detects malware and whether it is eliminated or needs further intervention. For PCs on a network, Portable Security for IoT has a centralized management program that can manage malware pattern files and configurations. It can also compile the scan logs of the scanning tools in multiple locations in an integrated fashion.
Trend Micro TippingPoint
The threat landscape continues to evolve both in sophistication and in technology. This means a new security system that is both effective and flexible is needed due to the dynamic nature of the landscape – one that allows you to tailor your security to meet the needs of your network. Selecting a network security platform is a critical decision because it serves as the foundation for advanced network security capabilities now and in the future. And, given the backdrop of the changing threat landscape, the importance of network security continues to increase, making it a difficult task.
Trend Micro TippingPoint Threat Protection System (TPS) is a network security platform powered by XGen™ security, a technology that offers comprehensive threat protection shielding against 12 vulnerabilities, blocking exploits and defending against known and zero-day attacks with high accuracy. It provides industry-leading coverage from advanced threats, malware, and phishing, and other threat vectors with extreme flexibility and high performance. The TPS uses a combination of technologies, including deep packet inspection, threat reputation, and advanced malware analysis on a flow-by-flow basis—to detect and prevent attacks on the network. The TPS enables enterprises to take a proactive approach to security to provide comprehensive contextual awareness and deeper analysis of network traffic.
Trend Micro Deep Discovery Inspector
Hackers often customize targeted attacks and advanced threats to evade your conventional security defenses and to remain hidden while stealing your corporate data, intellectual property, and communications, and sometimes to encrypt critical data until ransom demands are met. To detect targeted attacks and advanced threats, analysts and security experts agree that organizations should utilize advanced detection technology as part of an expanded strategy.
Deep Discovery Inspector is a physical or virtual network appliance that monitors 360 degrees of your network to create complete visibility into all aspects of targeted attacks, advanced threats, and ransomware. By using specialized detection engines and custom sandbox analysis, Deep Discovery Inspector identifies advanced and unknown malware, ransomware, zero-day exploits, command and control (C&C) communications and evasive attacker activities that are invisible to standard security defenses. Detection is enhanced by monitoring all physical, virtual, north-south, and east-west traffic. This capability has earned Trend Micro the rank of most effective recommended breach detection system for two years running by NSS Labs.
Trend Micro Deep Security
Virtualization and hybrid cloud computing can help your organization achieve significant savings in data center hardware costs, operational expenditures, and energy demands—while achieving improvements in quality of service and business agility. However, as data centers continue to transition from physical to virtual and now increasingly, cloud environments, traditional security can slow down provisioning, become difficult to manage, and cause performance lag. As you scale your virtual environment and adopt software-defined networking, evolving your approach to cybersecurity in productivity can reduce time, effort, and impact on CPU, network, and storage.
Trend Micro’s modern data center security is optimized to help you safely reap the full benefits of your virtualized or hybrid cloud environment. Our virtualization-aware security offers many advantages including performance preservation, increased VM densities, and accelerated ROI. Trend Micro™ Deep Security™ offers a complete set of security capabilities with the features you need to benefit from the efficiencies of virtualized environments and help meet compliance. This integrated solution protects physical, virtual, cloud, and hybrid environments.
Download this whitepaper to find out more about: real-world cyber attacks, reference architecture, OT security reference architecture, OT security domains and OT cybersecurity controls.
The whitepaper was written by Richard Ku & William Kam.
Richard Ku has over 23+ years of hands-on experience working in the hi-tech and security industry in a number of leading roles, as individual contributor and management. Currently served as SVP, IoT Security Business and Market Development for Trend Micro.
William Kam is Sr. Technical Marketing Manager at the same company.
Sorry, the comment form is closed at this time.





Pingback: Trend Micro Cybersecurity Reference Architecture for Operational Technology | Premium apps reviews Blog!
Pingback: Trend Micro Cybersecurity Reference Architecture for Operational Technology – indiz.de