Executive Order Issued to Improve the Nation’s Cybersecurity | SPONSORED
On Wednesday, May 12, President Biden signed the Executive Order on Improving the Nation’s Cybersecurity. Given the EO is 18 pages long and includes 74 actionable directives (many with due dates), it could take months to fully decipher and comprehend. Unfortunately, most companies don’t have months to understand how this EO will impact them.
aDolus has provided a quick summary of the key takeaways from the Executive Order.
Supply Chain Cybersecurity
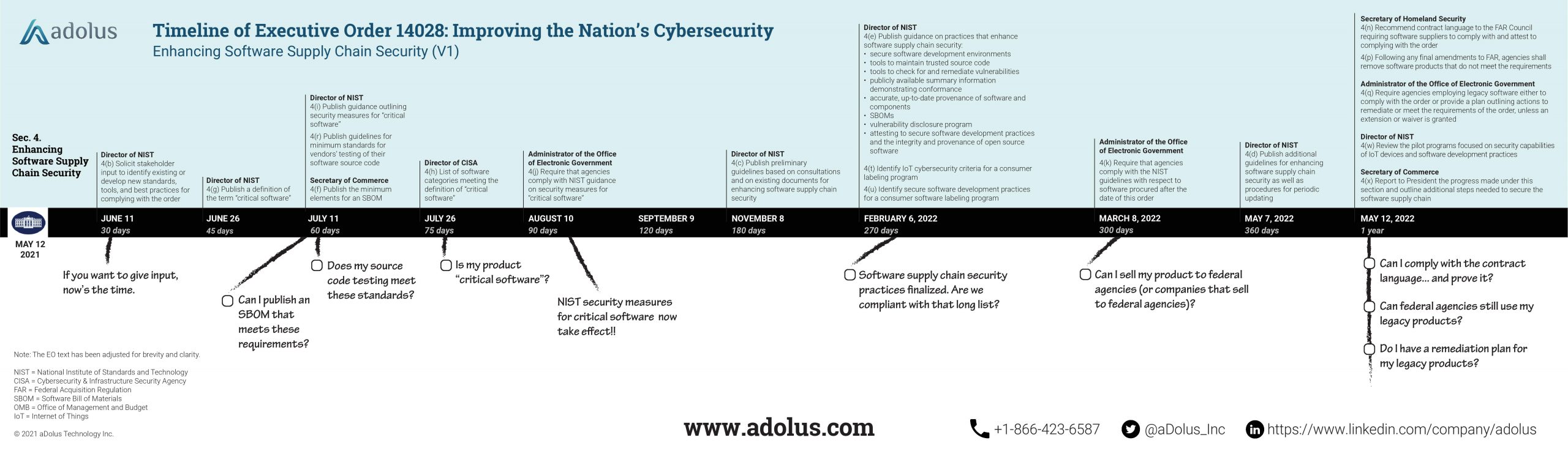
Securing the software supply chain is arguably the major focus of this EO. Almost one-third of the document’s policy statements are in the Enhancing Software Supply Chain Security section. This is no surprise after the SolarWinds attack in December infiltrated all five branches of the U.S. Military, the Pentagon, the State Department, the National Security Agency, the White House, and a whole lot of other significant targets. That kind of widespread havoc was certain to set the tone for this EO. (There are media reports suggesting this EO is a response to the Colonial Pipeline attack, but this document clearly wasn’t written over the weekend. Its scope is much further reaching and broader than ransomware attacks.)
The goals of this major initiative to secure the software supply chain aren’t obvious on first reading of the EO. But head to the accompanying EO Fact Sheet and four objectives stand out (taken directly from the Fact Sheet):
- The Executive Order will improve the security of software by establishing baseline security standards for development of software sold to the government…
- requiring developers to maintain greater visibility into their software and making security data publicly available….
- It stands up a concurrent public-private process to develop new and innovative approaches to secure software development and uses the power of Federal procurement to incentivize the market…
- it creates a pilot program to create an “energy star” type of label so the government – and the public at large – can quickly determine whether software was developed securely.
Read the full post from aDolus for more important takeaways from the Executive Order.