IoT Trustworthiness States
Confidence that an IoT system will operate in conformance with requirements results from assurance that several characteristics of the system are compliant with these requirements despite environmental disturbances, human errors, system faults and attacks. These characteristics – security, safety, reliability, resilience and privacy – have been identified by ISO/IEC (JTC SC41), National Institute of Standards and Technology (NIST) and the Industrial Internet Consortium (IIC) (Industrial Internet Security Framework (IISF), Section 3 as defining trustworthiness of a system. These characteristics manifest themselves in operational, organizational, commercial, budgetary, architectural and security areas.
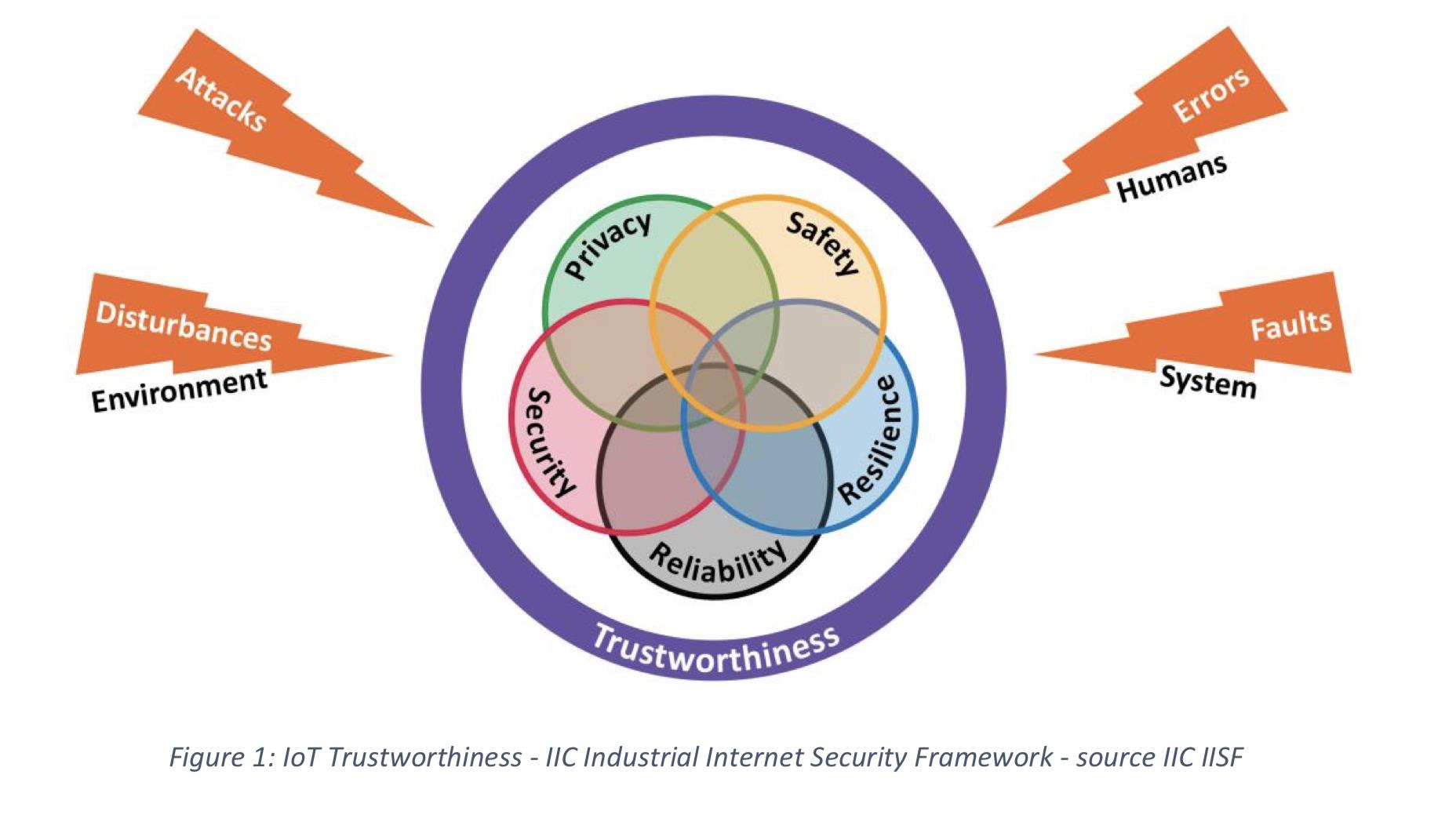
An IoT system is trustworthy if it meets the minimum requirements for security, safety, reliability, resilience and privacy, as defined by laws, regulations, standards and industry best-practices. The OSHA 29 CFR 1910 is an example of such regulation.
In general, trustworthiness has three milestone states:
Current State
This is the actual “trustworthiness” status of an IoT system, based on the system as it is currently designed, implemented and operating:
- Current state of safety processes
- Current levels of reliability and resilience
- Current state of data protection and security, as well as data privacy controls

Figure 3: The states of IoT Trustworthiness
The Current State evolves over time as the methods and processes put in place to address the trustworthiness requirements take effect and as factors such as system and human errors, lapses, cyberattacks, malicious activities and external influences begin to negatively impact the level of trustworthiness of the system.
Minimum State
This is a non-negotiable level of trustworthiness mandated by external authorities and parties; example, legal, regulatory and standards bodies, as well as industry best practices.
- To determine the Minimum State level, it will be important to assess applicable laws, regulations, best practices and standards, and evaluate their impact
- In situations where these requirements may conflict with each other, the organization’s Risk Management and Legal teams may need to be involved to provide opinions and guidance regarding the course of action.
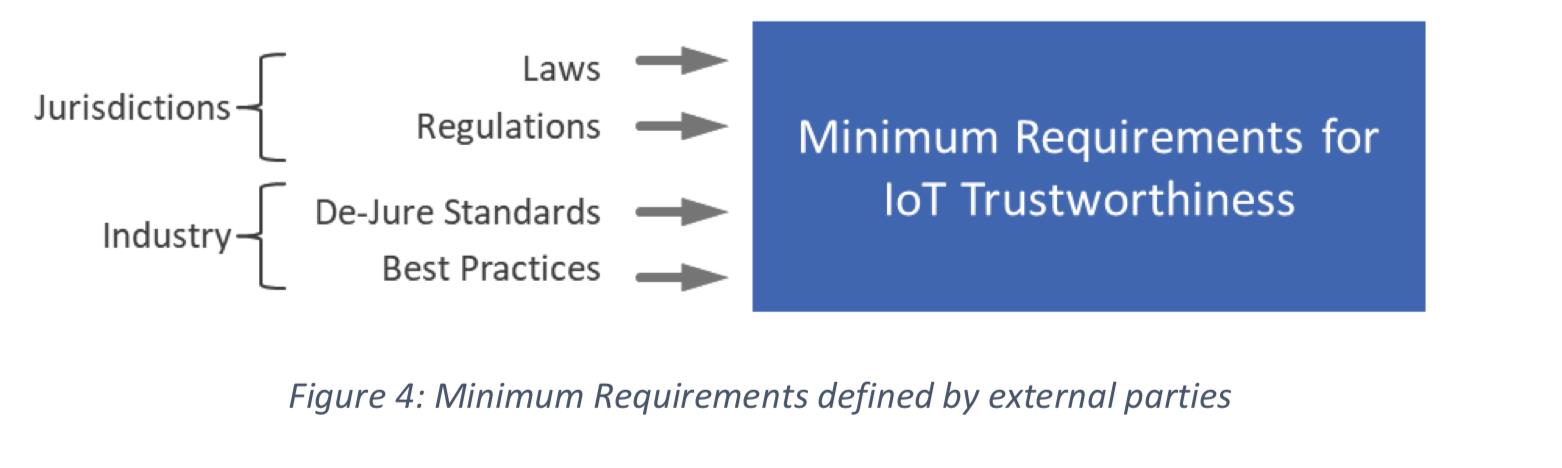
The IIC Industrial Internet Security Framework discusses some of the legal and regulatory requirements as they relate to Information Technology (IT) and Operational Technology (OT). Another example is the OSHA 29 CFR 1910 which covers occupational safety and health standards.
In addition to the above, requirements can have jurisdictional implications and in some cases actually boundaries (Data Residency). In these cases, the methods and processes implemented to empower the trustworthiness of the IoT system must have jurisdictional variations.
The EU General Data Protection Directive (GDPR) data privacy law came into effect on May 25th, 2018. It applies to Personal Data created and consumed within the EU jurisdictions as well as Personal Data belonging to EU residents anywhere in the world. The law imposes a wide range of restrictions on organizations (Data Controllers and Data Processors) that handle personal data. Personal data may be produced and consumed by an IoT system. Therefore the IoT Trustworthiness calculus must take into account the restrictions imposed by this law.
Other privacy law examples that apply within specific jurisdictions include the California Consumer Privacy Act of 2018 (CCPA) and the Personal Information Protection and Electronic Documents Act in Canada.
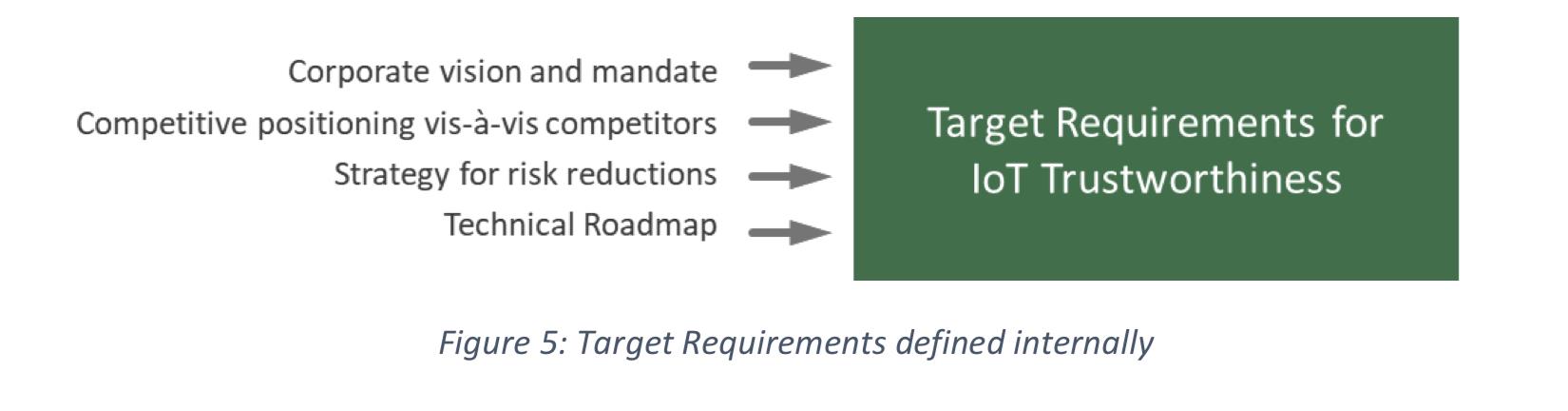
Target State
This third state represents trustworthiness levels that exceed the Minimum requirements, based on additional internally-defined and self-imposed drivers and objectives (business and technical):
More about Industrial IoT Law and Regulatory Aspects
This article was written by Bassam Zarkout, the CEO of IGnPower and originally was published here.