Trustworthiness methods in Industrial System Design
Trustworthiness in the context of an industrial system is a relatively new term intended to provide a better understanding of the meaning of trust in such a system and how this trust can be approached by the operational user as well as the planner and designer of the system. In general, the definition of trustworthiness by the Industrial Internet Consortium (IIC) is quite abstract and academic and of little help for the operation, planning or design of an industrial system. For example, the direct implementation of the five characteristics of trustworthiness into a concrete system is difficult or even impossible because these characteristics interact with each other and do not permit an isolated implementation of each. The five characteristics of trustworthiness are safety, security, privacy, reliability, and resilience.
The five characteristics of trustworthiness are not new in the history of industrial design. Figure 1 shows the history of these characteristics: They were introduced at different stages during the progression of the industrial revolution.
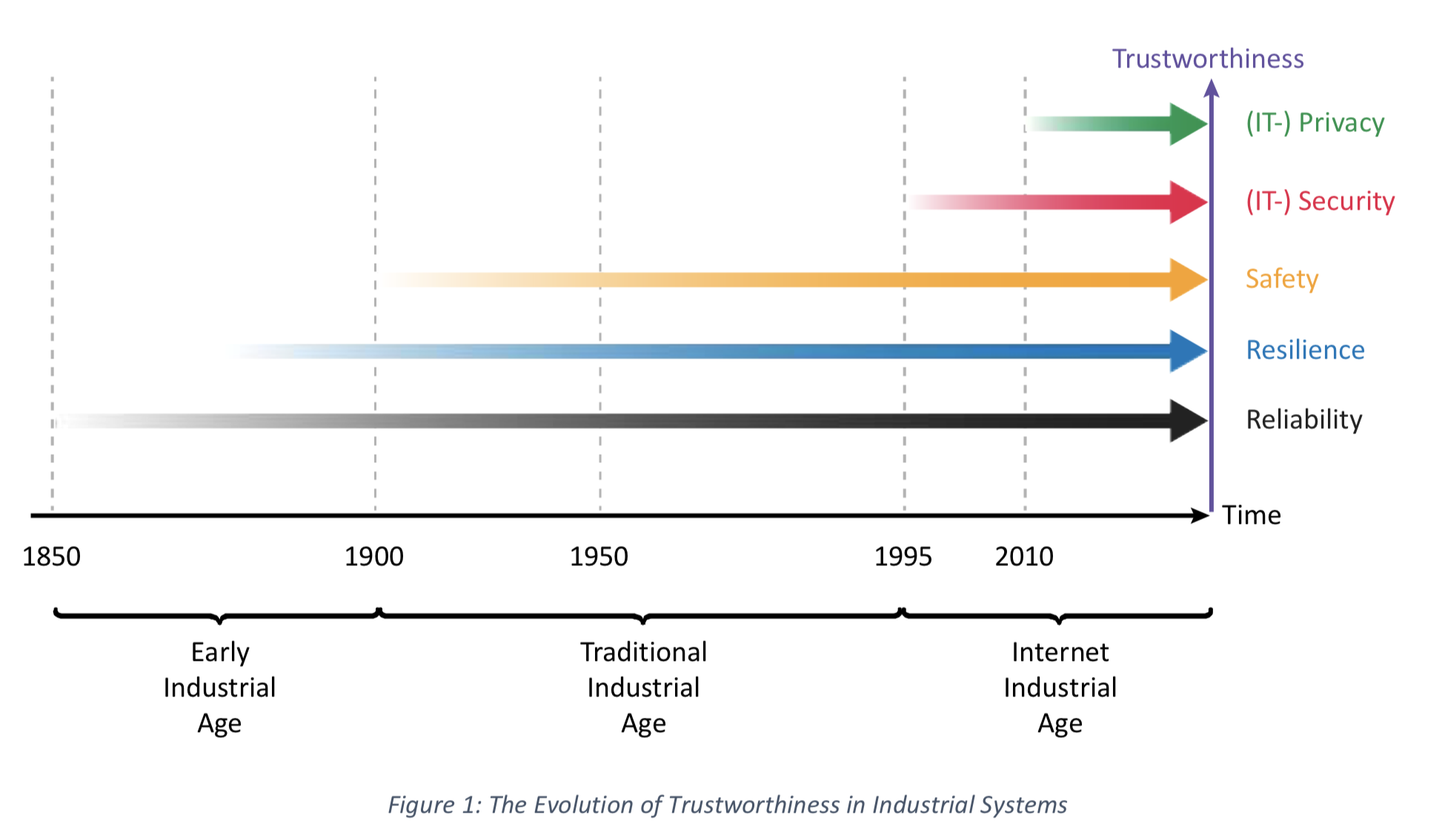
fig. 1
While most experts agree that the five trustworthiness characteristics and their interaction are an important goal for any industrial system design, there are ongoing discussions about whether a design which fulfills all requirements of trustworthiness can be automatically trusted by all parties. One way to answer the question is to analyze how these five characteristics address the specific targets which they protect. If the list of targets is complete and every target has at least one assigned Trustworthy Characteristic, the model’s completeness is proven. The Trustworthiness Target Model in Figure 2 demonstrates this graphically: There are four quadrants of targets which require a specific protection from harm:
- Humans (top left quadrant) represent not only customers (like patients in a hospital) but also employees, visitors or guests. It is obvious that privacy will protect this quadrant. But safety is also responsible to shield humans from harm. Security, reliability, and resilience of the system as part of trustworthiness, however, have no direct relation to this quadrant.
- Environment (top right quadrant) is exclusively protected by safety. It includes any natural aspects that are accessed by the system (e.g., pollution of air or water in nature), but also private neighborhoods and public infrastructure. No other trustworthiness characteristic directly addresses this quadrant.
- The System (bottom left quadrant) describes only the static system, including installed software and operational data, but not the operation itself. Security is responsible for its protection; resilience and to some degree reliability also protect the system against damage or loss of components, e.g., by fire or theft.
- Finally, the system in Operation is mostly shielded by security, reliability and partially resilience. The operational part of the system also includes the staff, e.g., being protected by security against human threats from outside.
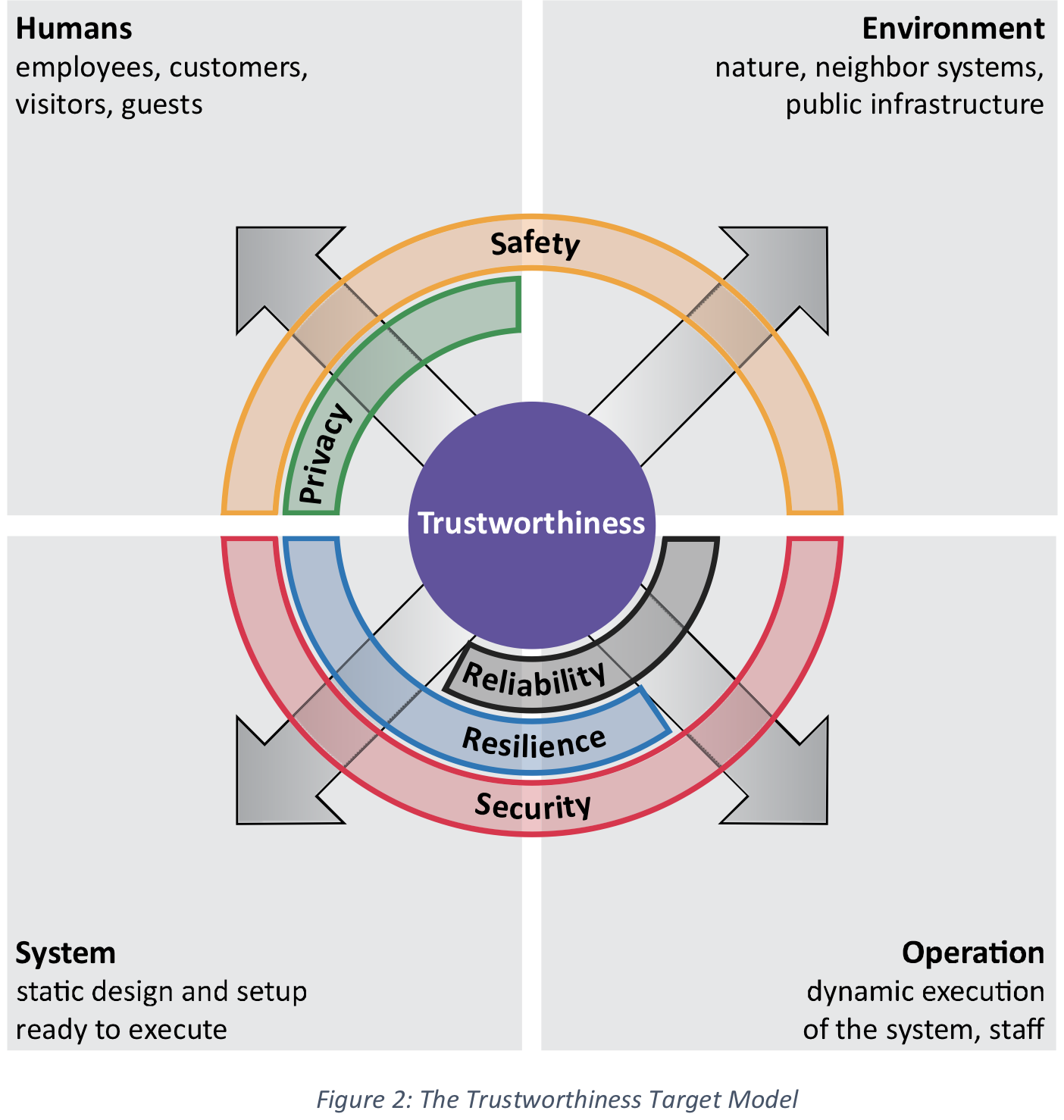
fig. 2
Employees are targeted in the Humans as well as in the Operation quadrant which may sound unusual. But, for example, every employee knows exactly when he or she has their yearly review meeting with the boss: The employee wears one hat for the personal expectation of receiving higher salary and benefits and another hat as a staff member agreeing to work with higher efficiency and better interaction with the rest of the team.
The complete vision of trustworthiness can be seen in these four quadrants: All important elements are protected. This model also shows that the five trustworthiness characteristics have sharp boundaries between their protected targets. This makes it easier to understand the design focus around each one of the five characteristics.
The reader may be confused by these sharp boundaries of trustworthiness characteristics between the four quadrants. For example: are not resilience functions typically installed in a system to prevent a disaster for humans and environment in case of a major system malfunction? The short answer is that such resilience functions are used to establish safety functions that ultimately protect the humans and environment; the resilience functions themselves do not provide the protections. The general answer will be provided by the concept of Trustworthiness Methods, introduced later in this article.
It is not possible to redirect the arrows in Figure 2 by 180 degree to ask the question “Who is threatening the trustworthiness of a system?” Simply stated, every member of the four quadrants threatens any of the five characteristics of trustworthiness: e.g., humans by making errors or attacks, the environment by disturbances and the system or operation by faults.
Read the full article by Marcellus Buchheit, President and CEO Wibu-Systems USA Inc. on IIConsortium website as it introduces Trustworthiness Methods and TSSM publicly for the first time. The author hopes for critical feedback from all readers in order to enhance and refine the explained models, providing a future trustworthiness model that is highly usable for practical design and operations of industrial systems.
For more resources on IIoT, access the ninth edition of the Journal of Innovation by The Industrial Internet Consortium here.



